This article will help in case you have received the alert “VA1219: Transparent data encryption should be enabled” while running the vulnerability assessment scanning for your Azure SQL managed instance.
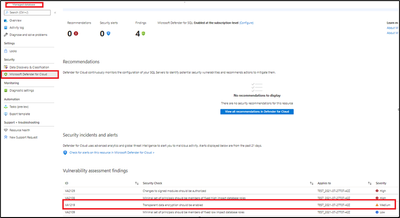
This alert can be viewed on your Azure portal under Security Incident Findings as below:
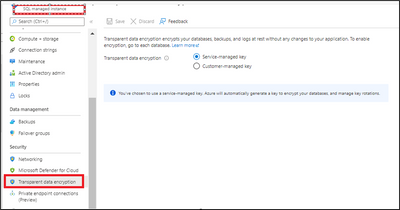
If you got this alert, this indicates that your Azure SQL managed database is not encrypted even if the Transparent Data Encryption (TDE) is set to service managed key or user-managed key as shown below:
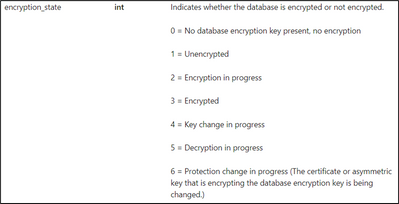
The alert could be shown for specific databases and not all the databases that are located under the same Azure SQL managed instance, and you can check the database status and its associated encryption keys by running the below script:
select * from sys.dm_database_encryption_keys
In case the database encryption_state is set to 1, it indicates that the database is unencrypted and you can have more information by accessing this link: sys.dm_database_encryption_keys (Transact-SQL) - SQL Server | Microsoft Docs.
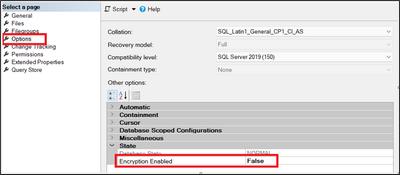
To resolve this alert, we need to verify the Encryption Enabled value from SQL Server Management Studio (SSMS) on the database level (SSMS -> database properties -> options), as below:
In case the shared query for a specific database was not retrieving any rows, and you are viewing the Encryption Enabled on your database level as False, then to resolve this alert you need to enable the Encryption Enabled on the database level to True and then to rerun the VA scan again.
The “Encryption Enabled” modification should not cause any downtime for your Azure SQL managed database and you can change it from SSMS directly. The Database encryption should not affect your workload but it might impact the performance around 3-5% as mentioned in this link.
More information
I hope this article was helpful for you, please feel free to share your feedback in the comments section.
Posted at https://sl.advdat.com/3J5Em6Thttps://sl.advdat.com/3J5Em6T