tl;dr - why would I care?
Connectors are often not only limited in their actions but also in terms of authentication. By calling the respecting API you have more freedom and can call a service with a Managed Identity. This sample shows how to deploy a simple Logic App that queries a Log Analytics workspace and connects to a SharePoint list
Intro
Azure Monitor Log Analytics is super powerful to collect data and give you insights on what’s going on with your apps and resources. There is even an Azure Monitor Logs connector for Logic Apps.
:high_voltage: Very unfortunately, the connector doesn’t support authentication with a Managed Identity - which means that you’d need either to be a signed-in user or use an app registration, which comes with its own challenges on secret handling. I explained in my previous blog posts why Managed Identities are a way superior way to authenticate.
Azure Log Analytics REST API to the rescue!
We can call the Azure Log Analytics REST API from Logic Apps with the generic HTTP action - and authenticate with a Managed Identity. For this example, I chose a user-assigned Managed Identity, so that you can reuse it across resources, but of course you can go with a system-assigned Managed Identity as well.
I wanted to create a sample on how to create a Logic App that queries Log Analytics with a user-assigned Managed Identity that has the Log Analytics Reader assigned. The Managed Identity also has Microsoft Graph permissions with scope Sites.ReadWrite.All assigned in order to create new items in a SharePoint list about the result of a query of Azure Monitor logs. That could be beneficial for users who don’t have access to the logs but should be notified or similar.
Deployment
- Fork and clone this repository
- Browse to the root folder in your clone
- Connect to the Azure subscription that you want this to run in
- Run the
deploy.ps1script, it will- create the resource group
- create the resources
- assign the
Log Analyticsrole to the Managed Identity - assign Graph API
Sites.ReadWrite.Allpermissions to the Managed Identity
- You will be prompted to provide
- a location for your resources
- a Resource group name
- the
siteIDof the site your list lives in - the
listIdof the list in which new rows shall be created
Validate deployment
-
Check in the Azure Portal after you read the success-message
Resources deployed successfully, role assigned- Resource group
- Logic App
- Azure Log Workspace
- Managed Identity
-
In the Logic App, the Authentication works with the Managed Identity
-
Our Managed Identity has the
Log Analytics Readerrole assigned -
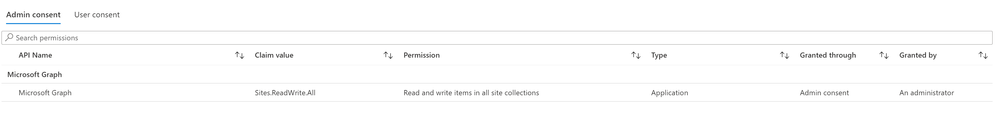
Our Managed Identity has the
SitesReadWrite.Allpermission assigned
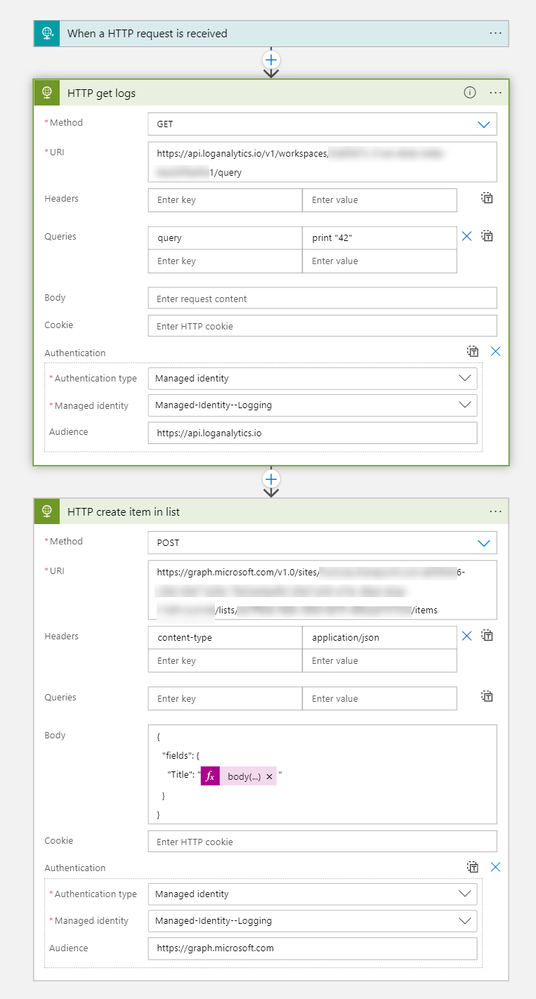
Our LogicApp should look like this:
Please make sure that you insert a query into the Logic app that makes sense depending on your scenario. Also adjust the body of the Create list item action to match your SharePoint list.
Conclusion
Connectors can be a good way to easily achieve what you need in Logic Apps. However, they sometimes don’t fit your scenario or don’t support your way of doing things - like I really like Managed Identities. Therefore, it's always worth a try to call the API directly so that you do not need to rely on the wrapper.
Questions?
If you have questions, want to use this, make it better - please do! Find me either on twitter or on GitHub
sharing is caring
Posted at https://sl.advdat.com/3KKkWpMhttps://sl.advdat.com/3KKkWpM