We are commonly receiving requests such as, how do I visualize MIP label usage? How can I use MIP label changes to trigger alerts? How do I get more detail on the sensitive information being processed at my endpoints? Is this data type being processed outside (or inside) of this geographical boundary?
We are pleased to share a new insightful way of pivoting risky behavior with organizational and geographical context. Meaning that you can start building risk profiles for your organization that can be used for both alerting and to be graphically presented as part of risk assessments of sensitive information use. You understand your organizations habits best, please treat this as a sample and expand based on your requirements.
The information is based on the new connector for CloudAppEvents for Sentinel, that ingests Microsoft Defender for Cloud Apps data. MIP label operations, processing of sensitive content on endpoints, dlp events, sharing events, file access events are all part of this event stream. Be aware that this will ingest a lot of events into Sentinel.
Let's take a sneak peak at a few of the things that the sample provides.
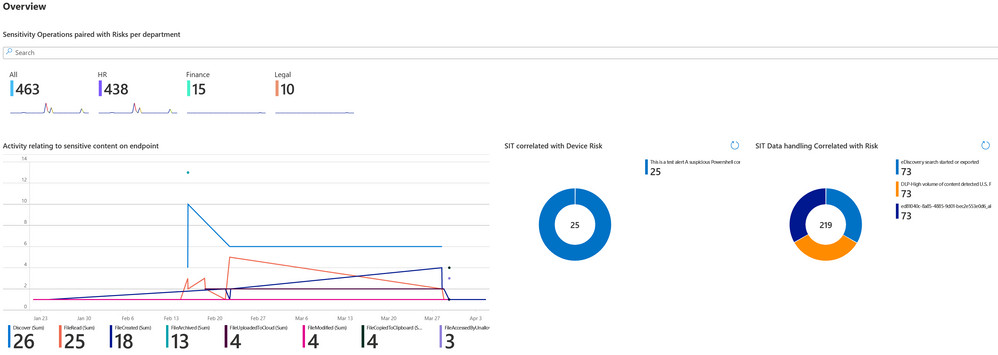
This is a view of Label operations and changes to labels, as well as some organizational context to how the labels are being used within the departments. There are several other views of label usage, the idea is that this serves as a starting point that you customize based on your needs.
The following is creating a view of the risk for the organization based on how sensitive information is being used on the endpoints. The logic is that SCC alerts or endpoint alert entities are joined with processing of sensitive information. In this case the HR users with ongoing incidents have also touched a lot of sensitive content which increases the overall risk. You should add your own IOCs (Indicators of Compromise), one part could be to add some detail in the user import that can be used for weight. Instead of departments you may want to level up to Division or slice it by the legal axis to present organizational exposure.
This view is not using risk correlation but displays the usage locations based on the ISP enrichment made to the MDE/Endpoint DLP events by Defender for Cloud App. Detail of the CloudAppEvent schema can be found here, there are plenty of more signals that can be used for hunting. The separate enrichment of Department is added as part of a Watchlist to allow for user data integration. This allows for understanding where most of the processing of sensitive information happens and the dominant SIT. SIT's with too high FP's or common use can be filtered out in the query.
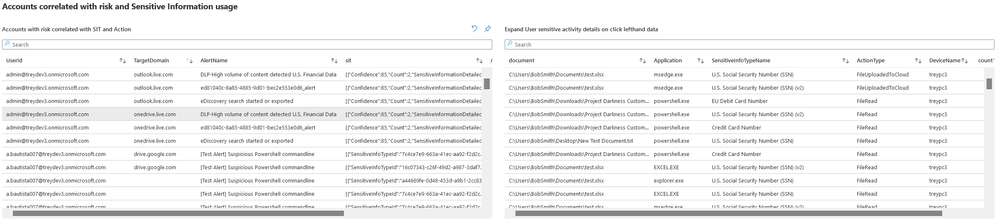
The following is a sample where one of the alerts correlated with sensitive data is clicked on the left hand. It expands the detailed information of the apps and types of sensitive data that have been processed by the user on the right hand side. In this case a lot of PowerShell access to sensitive content.
There are a few other reports in the pack that includes graphing of uploads and label use.
On top of this we have a few sample rules that can be customized based on how users interact with sensitive information. The lookback for security events is 30 days. This should be customized base on your security environment, it may provide false positives in its current setting. The Risky Device alerting is based on the Endpoint Microsoft 365 Defender alerts going in to Sentinel, you can use a similar query that works for alert correlation that you want to make.
Ideas for rules that you easily can create on top of these is "Sensitive content on Risky Device uploaded externally", "Sensitive content with a Risky Account uploaded externally"
How do I get started?
The signals used are based on Microsoft Information Protection events, Microsoft 365 Endpoint DLP/MDE and enriched by Microsoft Defender for Cloud. These are then connected to Sentinel via the new Microsoft 365 Defender connector. Select Microsoft Defender for Cloud Apps.
Ensure that you have connected the M365 Apps through Microsoft Defender for Cloud Apps to get the events flowing. You can also do this by checking that you have events coming in to CloudAppEvents in Microsoft 365 Defender advanced hunting.
We will make the following deployment steps easier over time. We plan to package it all to streamline deployment of the components below. The Watchlists are key for translating events from numeric to human readable, it is translating Label GUIDs to readable names and lastly we are importing all users, the reason for importing users and not using the built in AAD integration is that a lot of the data needed comes from HR systems or are in other custom fields.
Creating the Watchlists for user mapping and translation
Documentation for Watchlists https://docs.microsoft.com/en-us/azure/sentinel/watchlists
- Export the MIP labels using SCC Powershell, sample Get-Label | select ImmutableId,DisplayName,LabelActions | Export-Csv c:\tmp\slabels.csv -NoTypeInformation If you happen to get hyphens in the csv header fields, remove the hyphens since the WL engine cannot process.
- Create a new Microsoft Sentinel Watchlist call it Sensitive, set the ImmutableId as the index field.
- Import the csv generated in previous step.
- Create a new Microsoft Sentinel Watchlist call it MipMap, set the Value field as the index field, import the mipmap.csv file in this repo. (File to translate MIP operations)
- Create a new Microsoft Sentinel Watchlist call it UserAccounts, Import your account list, for reporting to work well you need to include, Userprincipalname,Department,FullName,Title,Country (The more detail you add the cooler you can make the report dashboard or any alerts), there is no normalization of the header so please capitalize the first letter as above or change the template.
- The Indexing field should be the UserPrincipalName, we use it as a key to enrich the items
- Import the csv generated in previous step.
Use the Microsoft Sentinel Large Watchlist to upload the list of users it scales well to 100's of thousands of users.
Creating the alerts and Workbooks
The analytics and workbooks can be deployed by clicking on deploy from within this repo, O365-ActivityFeed-AzureFunction/Sentinel_CloudApp at master · OfficeDev/O365-ActivityFeed-AzureFunction (github.com).
You will have to specify your Resource Group, and manually specify your Microsoft Sentinel Workspace.
On top of this don't forget to add Insider Risk Management and add IRM data to the all up risk exposure. We will add versions with both IRM and Microsoft Priva in the not too distant future.
Alerts from Microsoft Defender for Cloud Apps can also be used to inform Insider Risk Management, Microsoft’s solution for identifying and managing risky internal user activity. This integration allows security teams using Insider Risk Management to surface anomalous or potentially risky activity, like unusual mass deletion of content or suspicious admin activities observed via a connected cloud app (including via Amazon Web Services or Google Cloud Platform). To learn more about anomaly detection policies in Defender for Cloud Apps, visit our Microsoft Docs page: Create anomaly detection policies in Defender for Cloud Apps.
Happy hunting!
Posted at https://sl.advdat.com/3O3gx3phttps://sl.advdat.com/3O3gx3p