Do you need help with design, implementation, and monitoring of Zero Trust (TIC 3.0) workloads? Are you looking for technical solutions for visibility + automation of cloud, multi-cloud, hybrid, and on premises workloads? Do you have needs to implement solutions for Cybersecurity Executive Order requirements? This powerful tool can help organizations assess, monitor, and enhance their security posture relative to Zero Trust practices.

Since releasing the Microsoft Sentinel: Zero Trust (TIC3.0) Workbook in 2021, we have received overwhelmingly positive feedback from our user community. This group of over 5000 security professionals has shared their insights on the benefits as well as opportunities for further investigation and insights. Incorporating this feedback, we are excited to announce the next evolution of this content in the Microsoft Sentinel Zero Trust (TIC3.0) Solution.

This content features a redesigned user interface with new control card layouts and visualizations. Better-together integrations with Microsoft Defender for Cloud allow for assessments and alerting rules to actively monitor and alert on compliance posture deviations across each TIC 3.0 control family.
Solution Content
The upgraded Microsoft Sentinel: Zero Trust (TIC 3.0) solution contains a workbook, analytics rules, and a playbook. The Zero Trust (TIC 3.0) Workbook provides a single pane of glass for gathering and managing data to address control requirements across 25+ Microsoft products and 3rd party tooling. This aggregation at big data scale results in maximum visibility into on-premises, hybrid, and multi-cloud workloads with regards to relevant controls within the Zero Trust framework. This visibility empowers security architectures, engineers, SecOps analysts, managers, and IT professionals to gain situation awareness into the security posture of their hybrid and multi cloud workloads. Direct pivots to Microsoft Defender for Cloud recommendations allow for ease of correcting misconfigurations and hardening workloads against threats in accordance with zero trust requirements and practices.

Analytics rules further tap into Microsoft Defender for Cloud regulatory compliance mappings to measure Zero Trust alignment across each TIC3.0 control family and alert on deviations from an established baseline. The default configuration is set for scheduled rules running every seven days; alerting if posture compliance is below 70%. In response to these results, playbook can drive consistent, automated responses. This combination of analytics rules and playbooks allow for continuous monitoring and streamlined reporting that empowers teams to spend less time navigating across portals and more time focusing on remediation and getting secure based on collected insights from Microsoft Sentinel.
Solution Benefits
- Leverage policy, logging, live assets, and metrics to tell your Zero Trust story
- Design and implement Zero Trust (TIC 3.0) architectures
- Identify security blind spots
- Maneuver seamlessly through Microsoft 1st and 3rd Party offerings across cloud, multi-cloud, hybrid, and on-premises workloads.
- Document control status for Plan of Action & Milestones (POAMs) and System Security Plans (SSPs)
- Print/Save with single click report exports
- Respond and remediate security vulnerabilities
New Features
These new updates strive toward a singular dashboard to leverage Microsoft Sentinel and the greater security portfolio to understand security posture relative to zero trust principles. A streamlined experience, all access within the workbook provides a singular dashboard to navigate security operations and empowers teams to maximize time on remediation and getting secure. The updated iteration of this solution provides new capabilities to drive maximum visibility and reporting for cloud, multi-cloud, hybrid, and on-premises workloads:
- User Interface: Navigate your Zero Trust (TIC 3.0) architecture at scale from the new and improved user interface.
- Geolocation Enhancements: Correlation of Azure Active Directory locations for authentications, security alerts, sensitive data access.
- Network Mapping: Visualize and maneuver through your cyber key terrain with seamless pivots into Microsoft Defender for Cloud: Network Maps.
- Documentation: Attest to Security Leadership, Internal/External Auditors on Status of Control Compliance. Enhance System Security Plans (SSPs) and Establish Plan of Action & Milestones (POAMs).
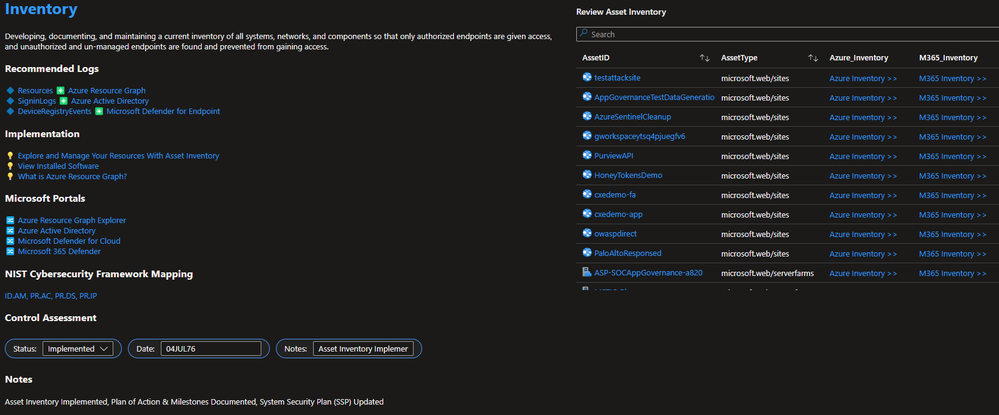
- Asset Inventory: Leverage Azure Resource Graph for Maximum Accountability of Hardware/Software Assets. Seamless Pivots to Azure and M365 Defender Inventory Pages for hardware, software, IoT tracking with Exportable Reporting.
- Better Together with Microsoft Defender for Cloud: Policy and posture assessments all-up, by control family, and by CMMC 2.0 Controls. Every policy recommendation contains a seamless pivot to remediation page and is reinforced with Solution alerting.
- System Baselining: Establish security baselines with Microsoft Defender for Cloud + Intune/Mobile Device Management. Track system configuration down to file, certificate, hardware, software, and registry key levels with pass/fail assessments and asset groupings.
- Access Control: Identify who, what, when, where, and how users/administrators are accessing your workloads, including trending, last sign-in location, and seamless pivots to Azure Active Directory profile pages.
- Security Incidents: Understand how you’re being attacked with alignment to Zero Trust (TIC 3.0) monitoring requirements. 3rd party integration across all of your security tooling ecosystem. Evaluate analyst efficiency, incident trending and measure response/remediation SLAs.
- Conditional Access: Monitor conditional access trending, application policy compliance, and blind spots in security architectures. Protect your applications, identify coverage gaps, and evaluate application access patterns.
- Security Orchestration, Automation, and Response: Inventory your SOAR Playbooks, identify triggers/trending over time. Highlight areas to mature automation capabilities. Seamless pivots to Microsoft Sentinel Automation for further configurations.
- Vulnerability Management: Assess each asset’s risk profile via high, medium, low and total vulnerabilities. Identify available patches and prioritize critical assets. Track CVEs and seamless pivots into asset pages for further configurations/response
Getting Started
Prerequisites
- Access Microsoft 365 Compliance Manager: Assessments
- Onboard: Microsoft Sentinel and Microsoft Defender for Cloud
- Add the Microsoft Defender for Cloud: NIST SP 800 53 R4 Assessment to Your Dashboard
- Continuously Export Security Center Data to Log Analytics Workspace
- Extend Microsoft Sentinel Across Workspaces and Tenants
- Review: Microsoft Service Trust Portal
Deployment
- Microsoft Sentinel > Content Hub > Search “Zero Trust” > Install or Update > Create > Configure Options > Review + Create
- Review Content
- Microsoft Sentinel > Workbooks > Search “Zero Trust”
- Microsoft Sentinel > Analytics > Search “Zero Trust”
- Microsoft Sentinel > Automation > Active Playbooks > Search “Notify-GovernanceComplianceTeam”, “Open-JIRA-Ticket”, “Create Azure DevOps Task”
- Review: ReadMe for additional Getting Started requirements.
- Feedback: Let us know what you think in the survey
Deploy today from Microsoft Sentinel: Content Hub
Learn more about Zero Trust with Microsoft Security
Bookmark the Security blog to keep up with our expert coverage on security matters and follow us at @MSFTSecurity or visit our website for the latest news and cybersecurity updates.
- Build and monitor Zero Trust (TIC 3.0) security architectures with Microsoft Sentinel
- Microsoft Zero Trust Model
- Announcing the Microsoft Sentinel: Zero Trust (TIC 3.0) Solution – Microsoft Tech Community
- Microsoft Sentinel Zero Trust (TIC 3.0) Solution on GitHub
- Zero Trust: 7 Adoption Strategies from Security Leaders
The Microsoft Sentinel Zero Trust (TIC 3.0) Solution demonstrates best practice guidance, but Microsoft does not guarantee nor imply compliance. All TIC requirements, validations, and controls are governed by the Cybersecurity & Infrastructure Security Agency. This workbook provides visibility and situational awareness for control requirements delivered with Microsoft technologies in predominantly cloud-based environments. Customer experience will vary by user, and some panels may require additional configurations and query modification for operation. Recommendations do not imply coverage of respective controls as they are often one of several courses of action for approaching requirements which are unique to each customer. Recommendations should be considered a starting point for planning full or partial coverage of respective control requirements.
Posted at https://sl.advdat.com/3jcytKMhttps://sl.advdat.com/3jcytKM
