Data exfiltration is often a primary goal during cybersecurity attacks. In 2021, over 80% of ransomware attacks threatened to exfiltrate data[1]. Adversaries target specific organizations with the goal of accessing or stealing their confidential data while remaining undetected, either to resell it on the dark web or to post it for the world to see.
Exfiltration during or before security attacks, mostly ransomware, happens mainly from endpoint devices. Researchers have observed adversaries leveraging legitimate file transfer utilities (FTUs) to upload sensitive data from devices to web services or cloud storage applications. Besides, adversaries generally try to evade simple security controls by renaming these FTUs.
Microsoft Purview Data Loss Prevention (DLP) for endpoint plays a major role in helping organizations detect and prevent exfiltration through common processes used by attackers today. If configured correctly, Microsoft Purview DLP can detect adversaries utilizing any FTU or cloud application to exfiltrate sensitive data from endpoint devices. Microsoft Purview DLP can also identify the execution of these tools when adversaries rename them to remain undetected.
Common tools/methods used to exfiltrate data
Most often attackers exfiltrate data by:
- Executing FTUs using command line to exfiltrate data over cloud applications
- Connecting to external networks
- Opening cloud applications on web browsers
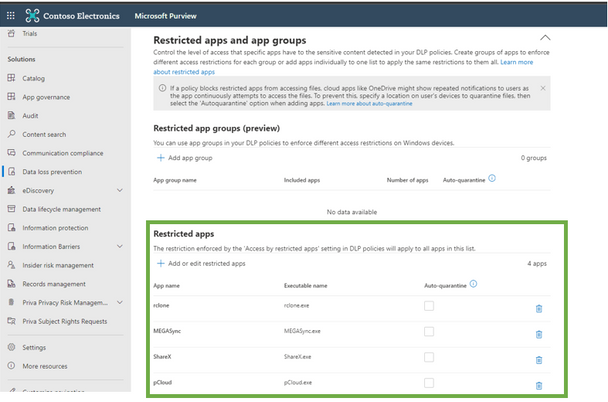
Some of the apps commonly used by attackers to exfiltrate data from endpoints are listed below. Configure these in your endpoint DLP settings today (steps below):
|
App name |
Executable name |
Description |
|
rclone |
rclone.exe |
Sync files to cloud storage |
|
MEGASync |
MEGASync.exe |
Cloud storage |
|
ShareX |
ShareX.exe |
Can be used: · As an open-source program to copy screenshots of data on clipboard and paste wherever required · To upload files to cloud storage |
|
filezilla |
filezilla.exe |
FTP solution |
|
pCloud |
pCloud.exe |
Cloud storage |
|
WinSCP |
WinSCP.exe |
SFTP |
|
PuTTy |
putty.exe |
Remote administration tool |
|
FreeFileSync |
FreeFileSync.exe |
File synchronization tool |
Table 1: list of apps commonly used by attackers
Steps to protect your data using Microsoft Purview DLP for endpoint
- Navigate to Microsoft 365 Purview compliance portal
- Select Data loss prevention from the left navigation and navigate to Endpoint DLP settings
- Add the above list of apps (see Table 1) in the “Restricted apps and app groups” section -> Restricted apps
- Create a DLP policy from the “Policies” tab and enable it for “Devices”
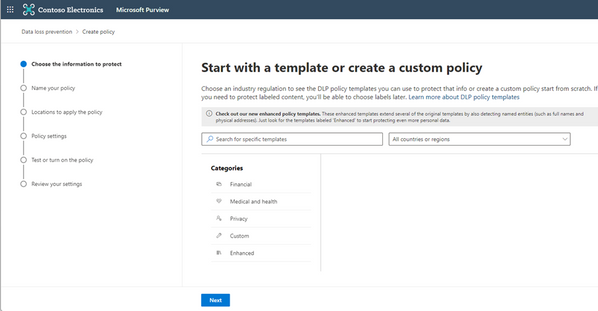
- Click on “Create Policy”
2. Select a template according to your need
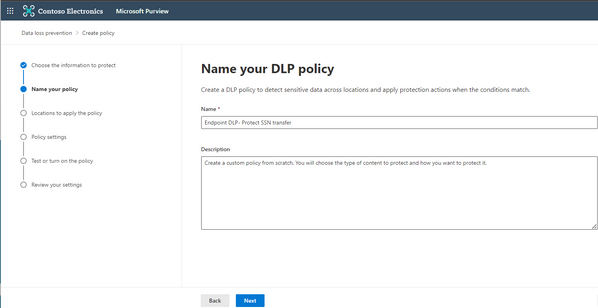
3. Provide a name and description of your policy
4. Select “Devices” to protect your endpoints
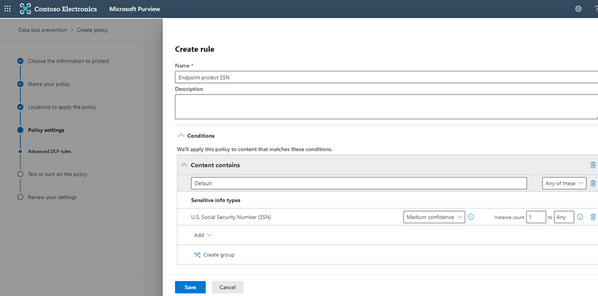
5. Create a rule
6. Add required Sensitive Information Type you want to protect/audit
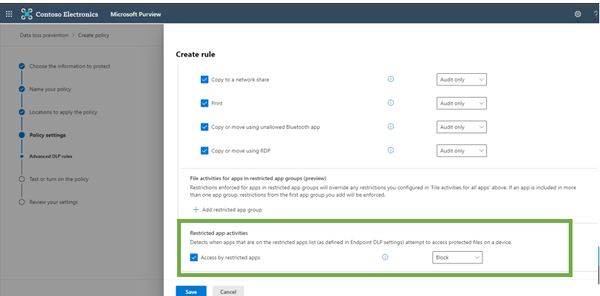
7. While creating a rule, add the restricted apps in “Actions” section
8. In “Restricted app activities” of “Actions” section, either Block/Audit these apps as per organizational need:
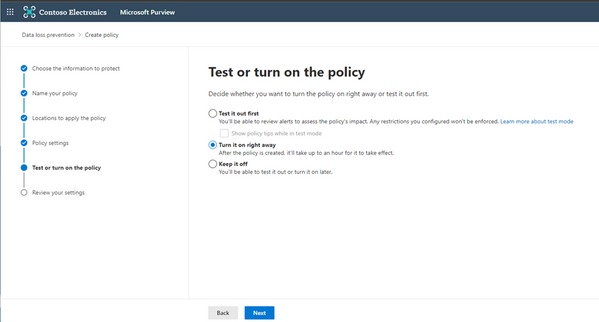
9. Test or turn on your policy
10. Monitoring and Remediation
An alert is generated and an audit log gets captured whenever any of the tools copy sensitive data to upload to cloud applications.
Note: This is captured only if a DLP policy is configured to detect the sensitive information that gets transferred (step 4).
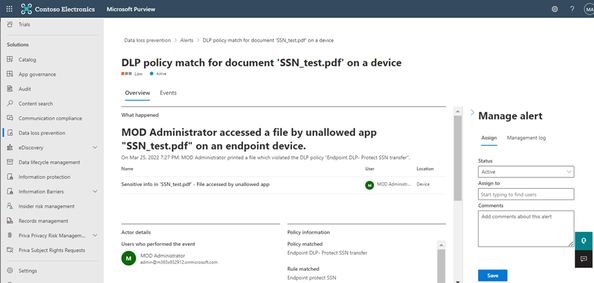
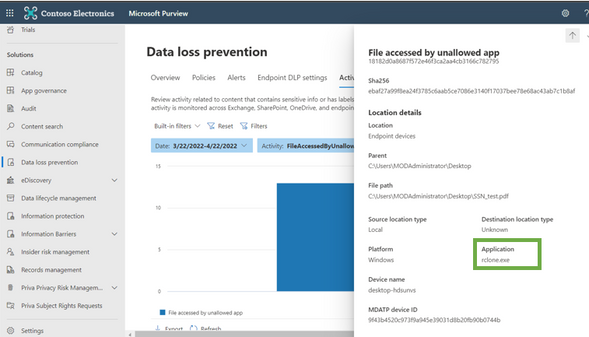
Experience of Policy match when rclone copies a sensitive file:
Audit log gets captured with the app name:
Renaming Tools
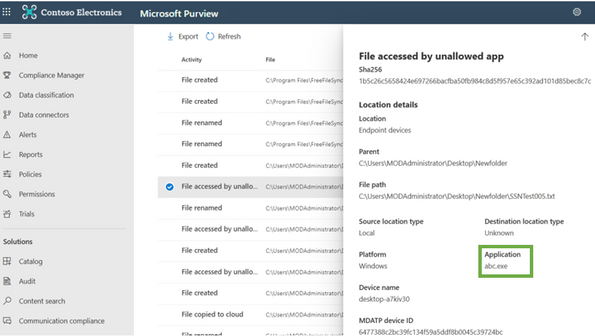
Adversaries frequently rename tools to evade detection. For instance, an adversary will rename rclone.exe to abc.exe to not get detected by traps/incidents. While matching against Restricted app list, Microsoft Purview Data Loss Prevention for endpoint picks up the original product file name instead of the renamed one, hence providing the leverage of detecting usage of these tools even after renaming.
For instance, let’s say adversary renamed rclone.exe to abc.exe and exfiltrated a sensitive file. Since the original product file name is not changed, Data Loss Prevention captures this renamed instance as well:
Get started
We are happy to share that there is now an easier way for you to try Microsoft Purview solutions directly in the Microsoft Purview compliance portal with a free trial. By enabling the trial in the compliance portal, you can quickly start using all capabilities of Microsoft Purview, including Insider Risk Management, Records Management, Audit, eDiscovery, Communication Compliance, Information Protection, Data Loss Prevention, and Compliance Manager.
Visit your Microsoft Purview compliance portal for more details or check out the Microsoft Purview solutions trial (an active Microsoft 365 E3 subscription is required as a prerequisite).
Additional resources:
- Read this blog to learn more about the Microsoft Purview announcement
- Watch these videos to learn more about Microsoft’s approach to cloud DLP, endpoint DLP, and maximizing the value of DLP
- Listen to this podcast on Microsoft Purview DLP.
- Learn more about using sensitivity labels as a condition for DLP policies here
- Learn more about sensitivity labels here
- Learn more about Predicates for unified DLP here
- Read this blog for the latest on Microsoft Purview Information Protection
We look forward to your feedback!
Thank you,
The Microsoft Purview Information Protection Team
[1] Anti data exfiltration vs Endpoint Security, BLACKFOG
Posted at https://sl.advdat.com/38Tm6l2https://sl.advdat.com/38Tm6l2