On December 2021 Microsoft announced its new solution for continuous monitoring for GitHub using Microsoft Sentinel. GitHub allows you to host, manage, and control different versions of software development using Git. It is highly important to track the different activities in the company’s GitHub repository, to identify suspicious events, and to have the ability to investigate anomalies in the environment.
Today we are thrilled to release a new OOTB content for the GitHub solution, additional analytic rules and a new workbook that was define from best practices.
In addition to the last analytic rules, Microsoft Sentinel released additional 10 analytic rules:
- Repository was created - this alert is triggered each time a repository is created in the GitHub environment that is connected to the Microsoft Sentinel workspace. In addition to the repository name, we get the actor who created this repository, so there’s an option to track the repositories and who is creating them.
- Repository was destroyed - this alert is triggered each time a repository is destroyed in the GitHub environment. It’s critical to track the repositories being destroyed in order to verify that the users destroying repositories have the correct permissions, and these actions are not part of a malicious activity.
- User was added to the organization - Organization owners can make anyone a member of their organization using their GitHub Enterprise Server username or email address. In cases that we have multiple organization owners we would like to track all new members on our organization, making sure we are aware of who’s contribute to our GH repositories.
- User was invited to the repository – after the organization owner has added the user to the organization, there’s an option to invite the user to specific repositories. This action is important so we can track all users who are invited to the different repositories and who has access to which repository.
- User visibility was changed - when you create a repository, you can choose to make the repository public or private. Repositories in organizations that use GitHub Enterprise Cloud and are owned by an enterprise account can also be created with internal visibility. There are also multiple options to change the user’s visibility. This alert raises once a user visibility changes.
- User was blocked - when a user is blocked from your organization the user stops watching your organization's repositories, they can’t comment or do any activity on the organization. We would like to know all the different users who got blocked from our repositories and our organizations.
- Two factor Auth disable – this alert is highly recommended to use, security-wise the 2FA is important for validation that the users who login are the real users and not hackers or attackers. Disabling this feature should be investigated and highly not recommended.
- Pull request was created - this alert raises once a PR is created to the different repositories on the organization that is connected to the sentinel workspace.
- Pull request was merged - this alert raises once a PR is merged to the repositories on the organization that is connected to the sentinel workspace.
- Activities from a new country – this alert identifies different activity’s locations within the same user, so if one user operates from one location and right after from a different location, this alert will notify us that for the same users there are multiple events from multiple locations.
The GitHub Audit Log workbook was modified as well and change according to best practices:
First we’ve added three different tabs to the existing workbook – repositories, integration installation and more.
The first tab, repositories, contains different statistics on the repositories on your GitHub workspace. We’ve added a time range filter which you can select the time frame you’d like to see the data on. for example how many repositories were created and how many repositories were renamed during the past 90 days:
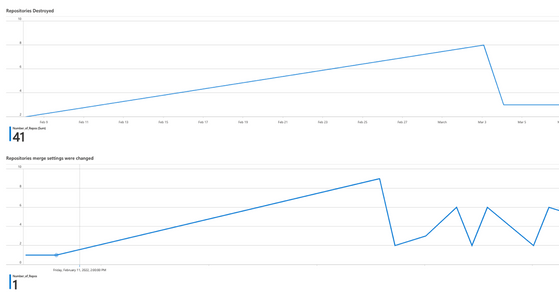
Another examples are how many repositories were destroyed and how many repository merge settings were changed during the past 90 days:
The second tab is integration and installation, this tab contains different charts regarding the configuration of the organization on the GitHub enterprise license which is connected to the Microsoft sentinel workspace. The time range filter is also affects the charts in this tab:
The third tab contains different analytics regarding the authentication and authorization of the different repositories – how many repositories dependency graphs were enabled and how many repository vulnerabilities alerts were enabled during the past 90 days (this number is configurable):
For more information, see:
- Microsoft Sentinel for GitHub - blog
- Microsoft Sentinel - Continuous Threat Monitoring for GitHub Solution
Posted at https://sl.advdat.com/3P7NNHjhttps://sl.advdat.com/3P7NNHj