We are excited to announce the general availability of a new set of APIs for Microsoft threat and vulnerability management that allow security administrators to drive efficiencies and customize their vulnerability management program. While previous versions were dependable and feature-rich, we built the new APIs with enterprises in mind that are looking for economies of scale within their vulnerability management program and need to handle large datasets and device inventories daily. These new APIs provide the ability to design and export customized reports and dashboards, automate tasks, and allow teams to build or leverage existing integrations with third party tools.
Security teams will get detailed information as part of a full data snapshot or they can limit the dataset to only include changes since the last data download for a more focused view. Information from the following threat and vulnerability management areas is included:
- Vulnerabilities assessment - discovered vulnerabilities on devices
- Secure Configuration Assessment - detected misconfigurations on devices
- Software inventory – a full list of installed software products across devices
Now let’s look at how you can use these new APIs to boost and customize your vulnerability management program.
Create custom reports
Customized reports and dashboards enable you to pool the most meaningful data and insights about your organization’s security posture into a more focused view based on what your organization or specific teams and stakeholders need to know and care about most. Custom reports can increase the actionability of information and improve efficiencies across teams, because it reduces the workload of busy security teams and allows them to focus on the most critical vulnerabilities.
Before building custom views using tools such as PowerBI and Excel, you can enrich the native datasets provided by Microsoft’s threat and vulnerability management solution with additional data from Microsoft Defender for Endpoint or a third-party tool of your choice.
In addition, these reports/dashboards give you an easy way to report key information and trends to top management to track business KPIs and provide meaningful insights on the overall status of the vulnerability management program in your organization.
With a custom interface you can show the information that your teams need and nothing more, creating a simpler task view or list of day-to-day work items. It provides flexibility in using any of the solution’s components, such as vulnerability report, missing security updates, installed software, end-of-support products, and operating systems, and combining them with advanced filtering capabilities. This can help optimize and streamline the end user experience according to your organization’s needs.
Let’s look at examples of reports that you can create:
Vulnerabilities report
This report gives you a snapshot of the security posture of your organization and allows you to identify the most critical and exploitable vulnerabilities, see the most exposed devices distributed by OS, or drill down into specific CVEs. You can user filters to show when a CVE was detected for the first time, or use advanced properties such as Device tags, Device groups, Device health (active\inactive), and more.


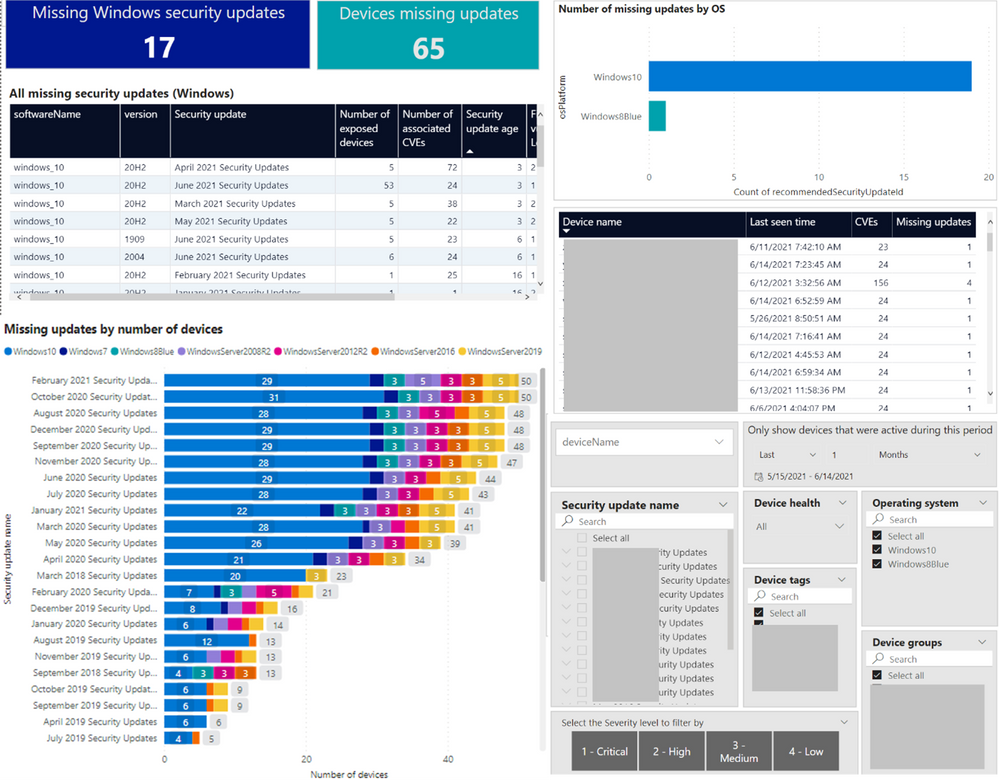
Missing Windows security updates
This report gives you a complete picture of all missing Windows security updates across your organization. You can see what the most exposed operating systems are, or search for a particular security update to show all affected devices.
You can filter the report by the associated CVE criticality, by age of each security update, or filter by advanced properties such as device tags, device groups, device health (active\inactive) and more.
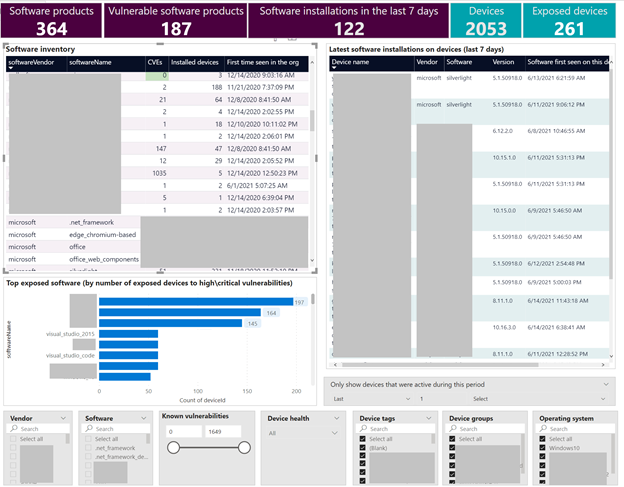
Software inventory
This report gives an overview of your software inventory. In addition to the org-level view, you can explore recent installations and on which devices, when, and in what version they were installed.
You can filter the report by number of the weaknesses associated with each software, by software name\vendor, or filter by advanced properties such as Device tags, Device groups, Device health (active\inactive) and more.
You can create your own reports, use any of the templates we have shown above, or check out more report templates in our GitHub library:
- End-of-support operating systems
- End-of-support software and versions
- Misconfigurations per device
- Software vulnerability recommendations
- Non-windows security updates
- Exposure score visualizations
Have you created your own report or used these published templates? We would love to see how you’re using these new capabilities!
Other resources:
Build OData queries with Microsoft Defender for Endpoint
Create custom reports using Microsoft Defender ATP APIs and Power BI
Automation and integrations
A big part of a successful vulnerability management (VM) program is the ability to automate tasks and reduce the manual workload of security and IT teams, as well as integrating the VM solution with existing tools that are part of an established workflow process in your organization.
Our new threat and vulnerability management APIs enable you to build a data exchange between natively provided data and your existing tools. At the same time, we are working with partners to continuously expand the portfolio of out-of-the-box integrations with third party solutions. You can already leverage our Skybox integration today and we are in the process of releasing additional integrations for ServiceNow VR and Kenna Security and in the coming weeks.
The Kenna Security partnership will strengthen the overall prioritization capabilities, combining threat and vulnerability management data with real-world threat and exploit intelligence and advanced data science to determine which vulnerabilities pose the highest risk to your organization. To learn more about the upcoming integration join our webinar on 6/24.
By integrating with ServiceNow Vulnerability Response you will be able to easily automate and track workflows. We will share more information soon!
While we will have more news on integrations and automation in the coming months, if there are specific integrations you would like to see on our roadmap, go to the Partner Application page in the Microsoft Defender Security Center, and click Recommend other partners.
More information and feedback
The threat and vulnerability management capabilities are part of Microsoft Defender for Endpoint and enable organizations to effectively identify, assess, and remediate endpoint weaknesses to reduce organizational risk.
Check out our documentation for a complete overview of how you can consume these new APIs.
We want to hear from you! If you have any suggestions, questions, or comments, please visit us on our Tech Community page.
Posted at https://sl.advdat.com/35lpxfi