With Azure Active Directory (Azure AD) identity governance, you can balance your organization's need for security and employee productivity with consistent processes and visibility. The new separation of duties checks feature now in preview in Azure AD entitlement management helps you prevent users from acquiring excessive or incompatible access rights.
Today, many organizations, such as those featured in our customer stories, use Azure AD identity governance entitlement management and access reviews features to set time limits for access, so users do not retain access to business-critical apps longer than necessary.
In entitlement management, you can bundle all project resources – groups, Teams, app roles, and site roles – into a single access package. If users need the Sales Executive role in a sales app, for instance, they can request an access package that includes that role. If approved, they’re also given access to a Team for discussion or a relevant SharePoint Online site for document storage. Once their assignment ends, their access is automatically removed.
Separation of duties checks is one of the top-requested additions to Azure AD for identity governance because it reduces risk exposure, preventing users from receiving combinations of permissions that could lead to misuse.
How the separation of duties checks feature works
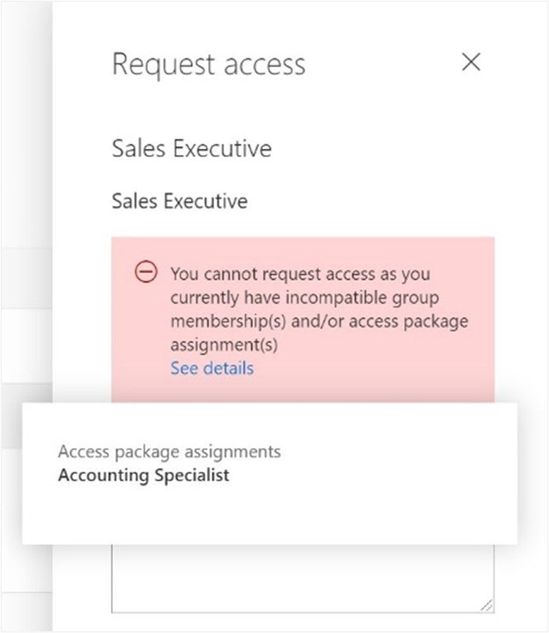
Imagine that in addition to a sales application, you have an accounting application. Your auditors are concerned that no one person should be able to change both sales and accounting data. They insist that all approval processes check that users requesting accounting access don’t already have sales access, and vice versa.
The separation of duties preview lets you prevent users from requesting an access package if they’re already assigned to other access packages or are a member of other groups. Configuring the access packages for sales and accounting so they’re incompatible — either through the Azure Portal or Graph API — simplifies the process. since approvers don’t need to manually check which assignments a user has.
Set up separation of duties checks in two steps
If someone with the Accounting Specialist access package visits the MyAccess page and requests the Sales Executive access package, they’ll be informed that their current access is incompatible. They can either give up their existing access, or request using a different access package with a different role.
Getting started takes just two steps.
- Add your applications — along with any groups, Teams, or sites —to an entitlement management catalog and set up your access packages. If using Azure, you can also add security groups assigned to Azure roles.
- Configure the separation of duties checks preview on those access packages. You can then follow the Azure AD audit log or use the Azure Monitor access package activity and application role assignments workbooks for reports on how users got access.
We’d love to hear your feedback, whether you’ve just tried this preview or have already been using entitlement management or other Azure AD identity governance features. Share comments and suggestions below or on Twitter.
Learn more about Microsoft identity:
- Return to the Azure Active Directory Identity blog home
- Join the conversation on Twitter and LinkedIn