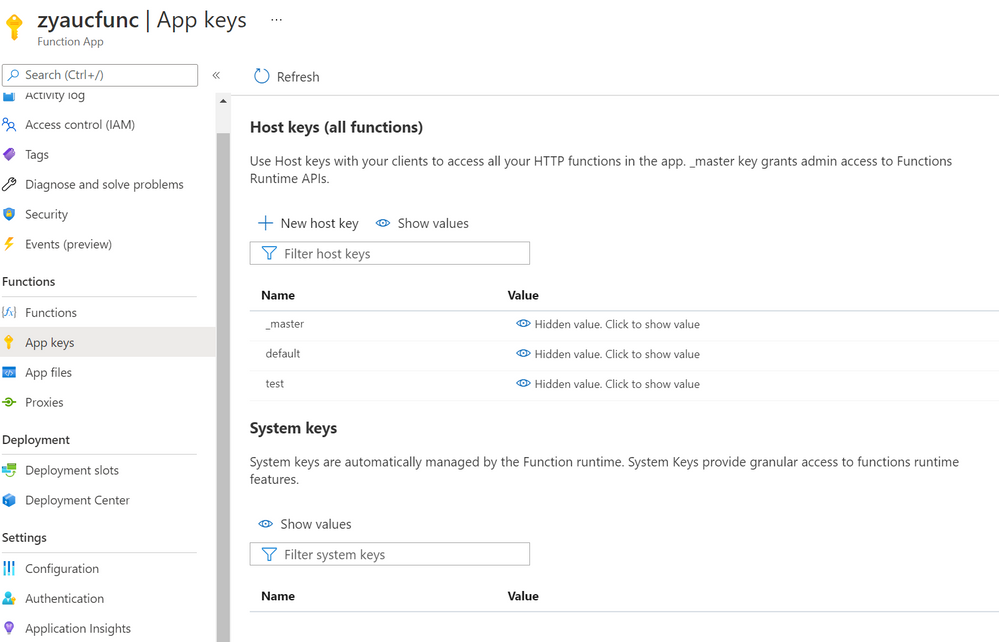
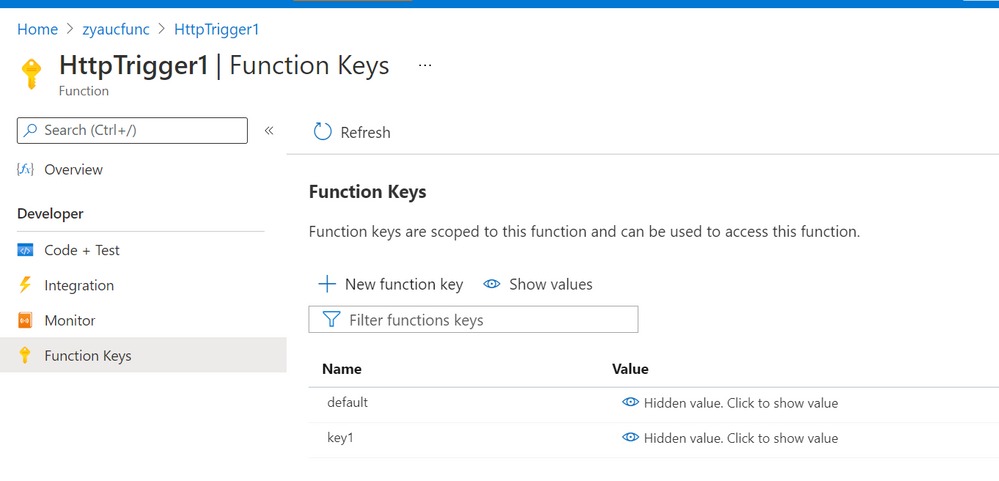
When running Azure function apps, we need function keys to access the functions. By default, the function keys of a function app are stored in a storage account, which is specified in the appsetting ‘AzureWebjobsStorage’. You can view the keys in portal as shown below.
Fig 1. Host keys of function apps in portal
Fig 2. Function keys of a function in portal
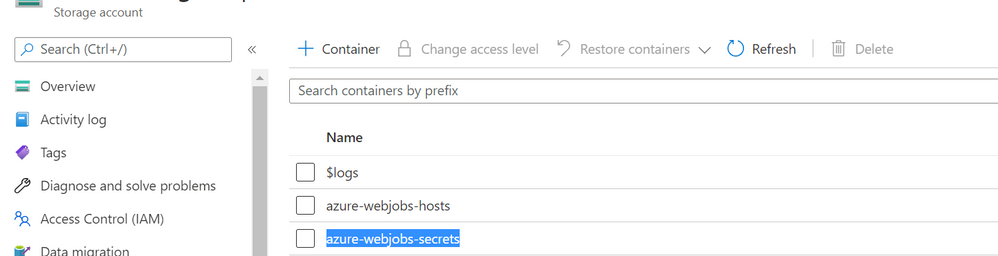
If you go to the storage account specified in appsetting ‘AzureWebjobsStorage’, you can find the function keys in container ‘azure-webjobs-secrets’. You can see the below container where keys are stored.
Fig 3. The container where function keys are stored in the storage account
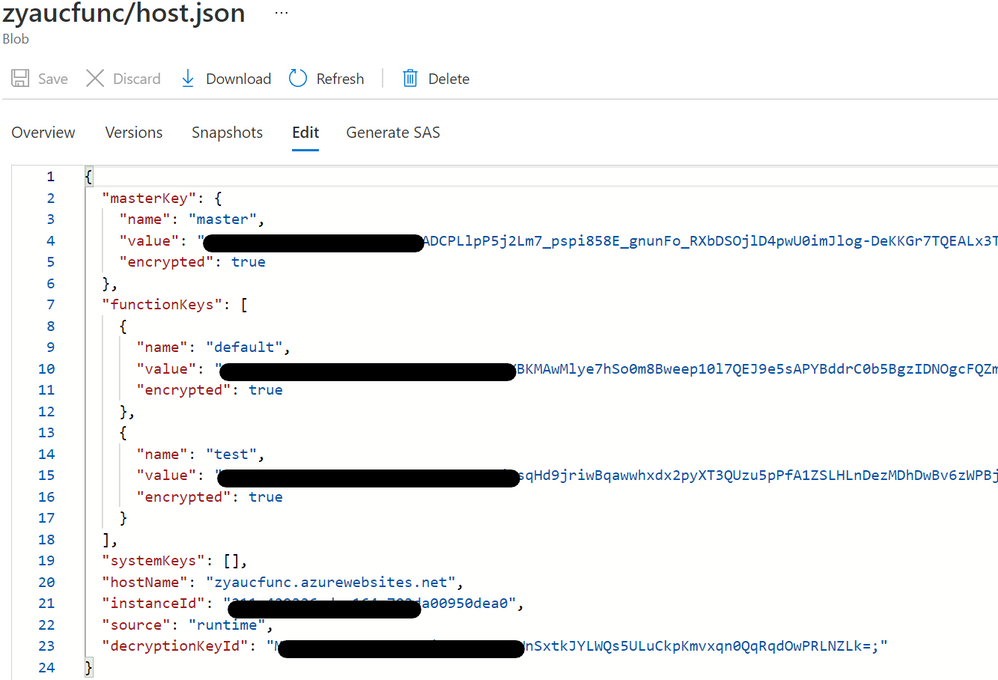
In the container, you can see the file ‘/{functionAppName}/host.json’, where function keys are stored.
Fig 4. The host.json file where function keys are written
Instead of a storage account, we can also choose a key vault to store function keys. Below are the detailed steps.
Solution:
1. At first, add below two appsettings to the function app.
|
Appsetting Name |
Value |
|
AzureWebJobsSecretStorageType |
keyvault |
|
AzureWebJobsSecretStorageKeyVaultName |
<key vault's name> |
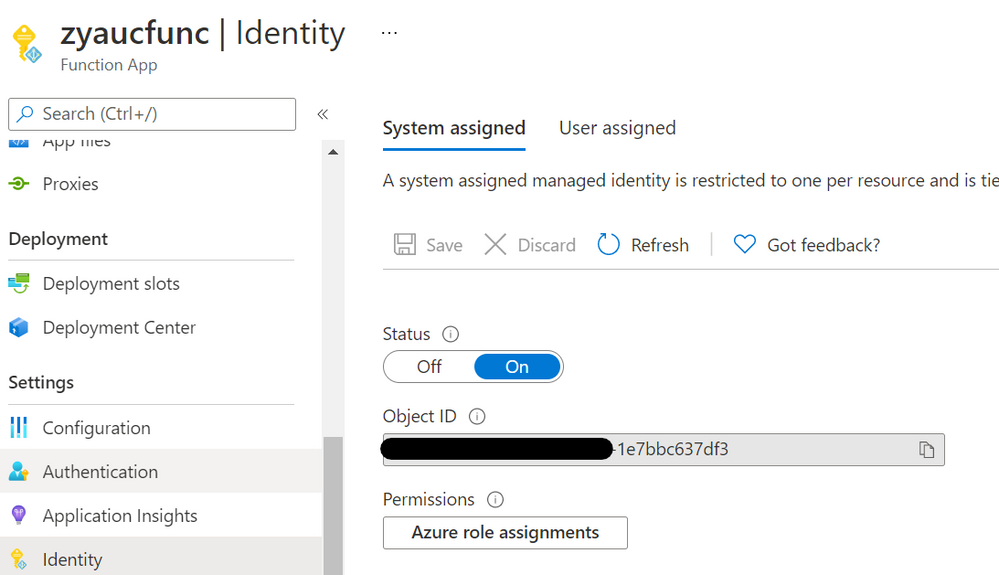
2. Enable managed identity in ‘Identity’ blade of the function app in portal.
Fig 5. Enable managed identity of a function app.
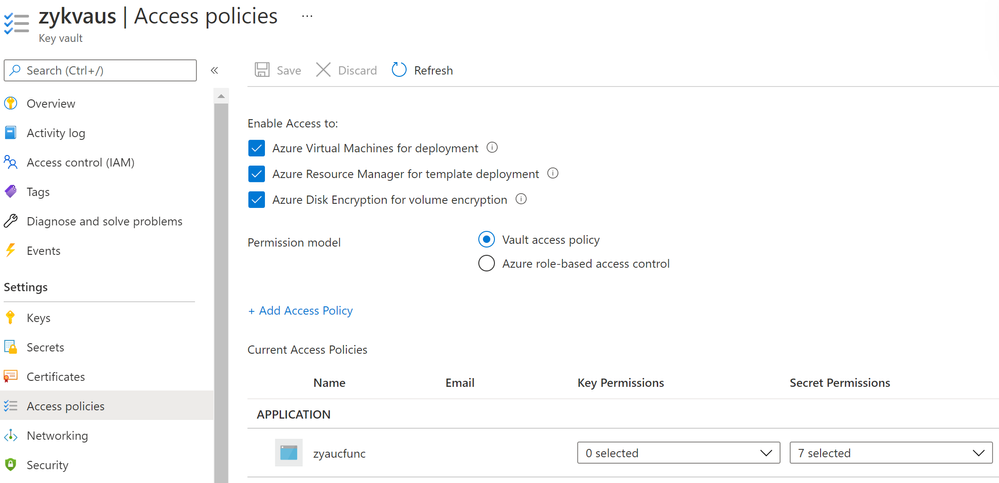
3. Go to ‘Access Policies’ blade of the key vault in portal, add an access policy for the function app using the app’s managed identity. You need to give the function app at least the secret management permissions.
Fig 6. The access policies blade of the key vault.
Fig 7. Select your function app in ‘Select principal’, and give it the certificate management
4. You had better restart the function app to let the settings make sense immediately.
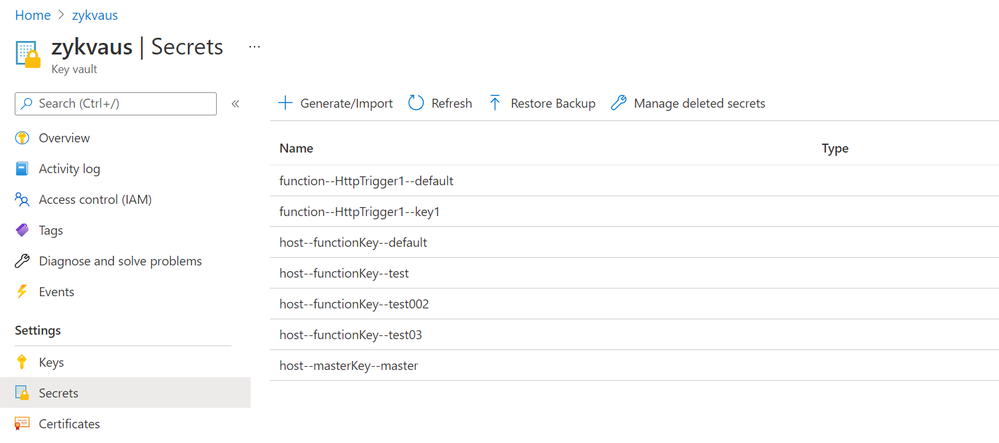
5. Now when you add or delete host keys or function keys in portal, you will see the function keys in ‘secrets’ of the key vault.
Fig 8. Host/function keys stored in key vault.
Hope this article will be useful to you! Thanks for reading!
Posted at https://sl.advdat.com/37xSsxM