Introduction
In today’s era of growing cyber-attacks, Cyber Threat Intelligence (CTI) is a key factor to help Security Operations Center (SOC) analyst triage and respond to incidents. Azure Sentinel is a cloud native SIEM solution that allows customers to import threat intelligence data from various places such as paid threat feeds, open-source feeds, and from various threat intelligence sharing communities like ISAC’s. Today we are announcing the General availability (GA) of Azure Sentinel Threat Intelligence in Public cloud and Azure Government cloud within 30 days from today.
Azure Sentinel supports open-source standards to bring in threat intelligence data into the product like STIX/TAXII. STIX is the data format and TAXII is the sharing protocol widely used in the industry for the purpose of sharing threat intelligence data. Azure Sentinel is one of the major adopters of STIX/TAXII 2.x and promotes this industry standard for sharing threat intelligence data.
Azure Sentinel also offers a first-class UI to create, search, sort, filter, and tag threat intelligence data in the product without writing any queries.
In this blog, we will cover:
- Easy ways of getting threat intelligence data using TAXII data connector
- Management of threat intelligence data in Azure Sentinel
- Putting threat intelligence to use with out-of-the-box analytic rules
- Getting insights into threat intelligence with Workbooks
Enable the Threat Intelligence – TAXII data connector in Azure Sentinel
STIX/TAXII is the most widely used industry standard for sharing threat intelligence data. STIX is the data format and TAXII is the protocol used to share threat intelligence data. Azure Sentinel offers a built-in TAXII client to import threat intelligence data from TAXII 2.x servers in the form of a data connector.
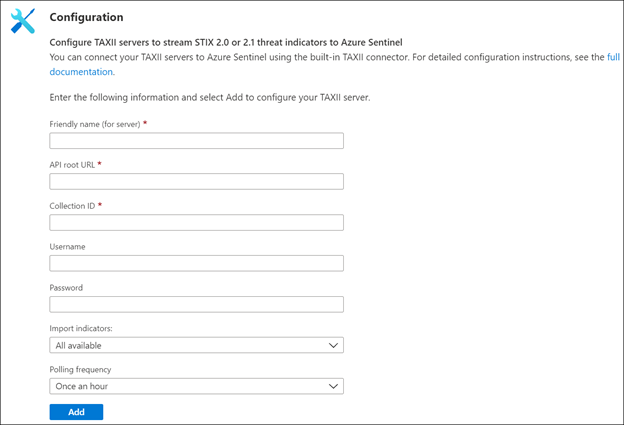
To import threat intelligence data from a TAXII 2.x server into Azure Sentinel, navigate to the TAXII data connector page under the Data connector gallery of Azure Sentinel.
To learn how to configure Threat Intelligence - TAXII data connector in Azure Sentinel step by step visit the Threat Intelligence – TAXII documentation.
Manage threat intelligence data in Azure Sentinel
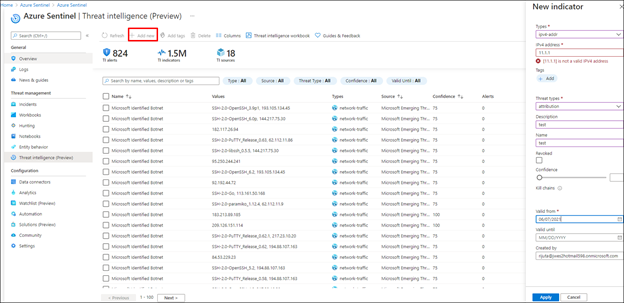
The Threat Intelligence blade in Azure Sentinel is a one-stop location to create, view, search, sort, filter, and tag threat intelligence indicators. This area allows creation of threat intelligence indicators from within the Azure Sentinel interface. Tagging of indicators of compromise (IOC) is also possible from this area. This helps grouping of IOC’s and relating IOC’s to a particular cases and incident. Searching, filtering, and sorting of threat intelligence data is also available in the product.
To learn more about how to create, tag, and filter indicators refer to the documentation here.
Put threat intelligence to use with out-of-the-box analytic rules
Now that threat intelligence data has been imported into Azure Sentinel, it can be used to power analytics to match it against log data which will generate actionable alerts and incidents. SOC analysts can then use these incidents to take actions and prevent organizations against threats.
Customized analytics rules can be created, or Azure Sentinel offers 26 out of the box analytic rules for matching threat indicators imported/created in Azure Sentinel with log data. The out-of-the-box analytic rules are scheduled KQL based rules and begin with the keyword “TI map”. One such example is “TI map IP entity to OfficeActivity” which matches all IP indicators imported into Azure Sentinel with Office Activity logs.
To learn how to enable and create analytic rules, follow the steps mentioned in this documentation.
Get insights into threat intelligence with Workbooks
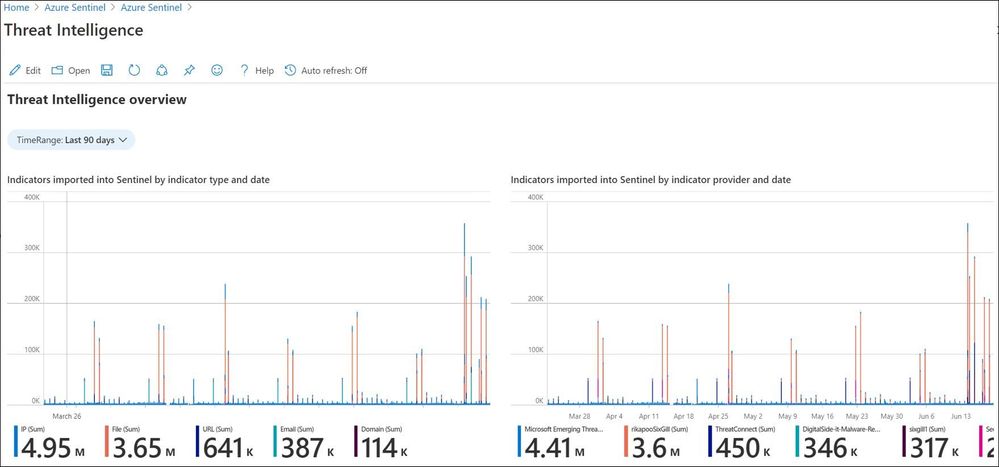
Azure Sentinel Workbooks are visual charts toobtaininsights into data. Azure Sentinel offers an out of the box workbook called the“Threat intelligence”workbook to getinsightsabout threat intelligence data.This workbook is completely customizable and offers some chartswhichtell about the incidents generated with threat intelligence dataandfeed uniqueness about the feedsbroughtinto Azure Sentinel irrespective of the source.
Workbooks are great interactive charts to get insights on threat intelligence data like feed uniqueness of TI providers which is important for analysis and understanding of paid feeds. This is a newly added chart to the Threat Intelligence workbook.
Conclusion
With this release of the Azure threat intelligence to General Availability, customers now have a full suite of TI capabilities in Azure Sentinel to advance the SOC TI program and fully utilize the power of TI within the SIEM. Over the next couple of months, more threat intelligence enhancements will be released in Azure Sentinel. The major advantage of threat intelligence being in General Availability is the ability to use them in various clouds like Public and Azure Government clouds.
Posted at https://sl.advdat.com/39IVIra