If you utilize them all together, Azure Landing Zones, Azure Policy, Azure Security Benchmarks, and the CMMC Level 3 Initiative in Azure Security Center can ease your CMMC compliance journey. In this blog, we'll show you how!
Microsoft is actively building out our program by developing resources for both Partners and Defense Industrial Base (DIB) companies to leverage in their Cybersecurity Maturity Model Certification (CMMC) journey. These tools and guidance cannot guarantee a positive CMMC adjudication, but they may assist candidate organizations by improving their CMMC posture going into a formal CMMC review in accordance with CMMC Accreditation Body (CMMC AB) standards. While we plan to release resources and guidance in waves, please keep in mind we are dependent upon the CMMC AB finalizing the CMMC guidance itself. As a result, there may be additional nuance or complexity associated with CMMC compliance that will only materialize (if at all) through the practical application of the standard by the CMMC AB. What’s more, as of the date this post was written, the CMMC AB has not issued formal guidance for Cloud Service Providers. As a result, the information herein, including all Microsoft CMMC related offerings, are provisional and may be enhanced to align with future guidance from the DoD and CMMC AB. Microsoft does not guarantee nor imply any ultimate compliance outcome or determination based on one’s consumption of this post—all CMMC certification requirements and decisions are governed by the CMMC AB, and Microsoft has no direct or indirect insight into or bearing over CMMC AB compliance determinations.
Aligning CMMC Controls with your Azure Landing Zone
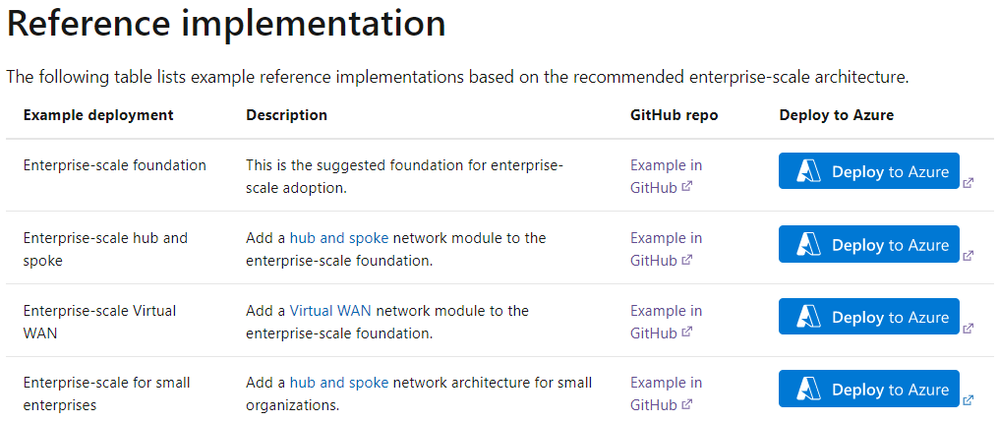
Azure Landing Zones (ALZ) enable application migration, modernization, and innovation at enterprise-scale in Azure. The Microsoft Cloud Adoption Framework’s reference architecture and implementations, known as Enterprise-Scale Landing Zones, helps you deploy an Azure foundation that is scalable, operational, and extendable by design. Even when you have been deployed in Azure for a while and attained a level of maturity, the framework serves as a design to realign to Azure recommended practices and identify and address any technical debt accumulation. The below table shows the available Enterprise-Scale reference implementations.
Additionally, the Enterprise-Scale reference implementations have been aligned closely with Azure Security Benchmarks (ASB) and grant some assurance that the landing zone that is deployed will be compliant with Microsoft’s defined security benchmarks. We recently mapped the CMMC Level 3 controls to the ASB so that customers needing alignment with CMMC can also leverage the ASB to assist in determining whether the landing zone meets compliance requirements. This ASB mapping to CMMC may be downloaded here: https://aka.ms/cmmc/asbmap. In addition to aligning CMMC to ASB, we have also mapped ALZ policies to CMMC controls. By combining an ALZ implementation with Azure Policy, Azure Security Benchmarks, and the CMMC compliance initiative, you can attain a reference implementation and get visibility into CMMC alignment. This blog post will cover the Azure Landing Zone architecture, CMMC mapping to ALZ policies, and the compliance audit and reporting options found in Azure Security Center.
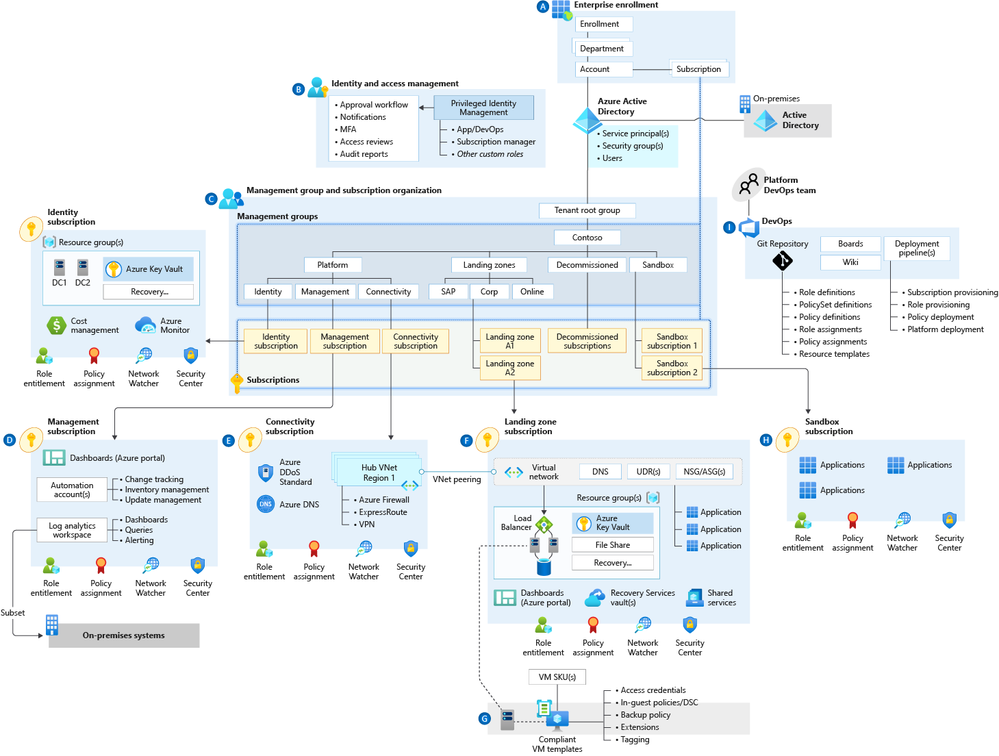
High-Level Azure Landing Zone Architecture
An ALZ enterprise-scale architecture is defined by a set of design considerations and recommendations across eight critical design areas, with two recommended network topology options: an enterprise-scale architecture based on an Azure Virtual WAN network or an architecture based on a traditional Azure hub and spoke network topology (depicted below).
One of the core design principles of Azure Landing Zones is policy-driven governance. This means that Azure Policy provides guardrails for your organization's Azure platform, along with the workloads deployed onto it. Azure Policy also provides application owners with both sufficient freedom and a secure unhindered path to the cloud.
There is a large set of guardrails that come out-of-the-box with an ALZ implementation. To increase flexibility, not all these policies are associated during the landing zone deployment. Therefore, each policy should be well understood and evaluated against your corporate standards to enable you to achieve the appropriate impact to how open or locked down you want to make your landing zone deployment. After evaluation, the policies can either be associated during your ALZ deployment in a CI/CD pipeline or configured through the portal after your deployment is complete. Also, whether you are greenfield or brownfield, the AzOps Accelerator, Microsoft’s integrated CI/CD solution, can help you manage your environment at scale.
Mapping CMMC Controls to Azure Landing Zone Policies
As mentioned above, the Azure Landing Zone deployment includes a set of policies to enforce guardrails using a policy-driven governance approach. We have aligned these ALZ policies to the CMMC Practices and CMMC ID# as shown below. This mapping provides guidance to assist you with implementing CMMC controls when deploying your Azure landing zone. This Azure Landing Zone mapping for CMMC may be downloaded here: https://aka.ms/cmmc/alzmap
Applying the CMMC Initiative in Azure Security Center
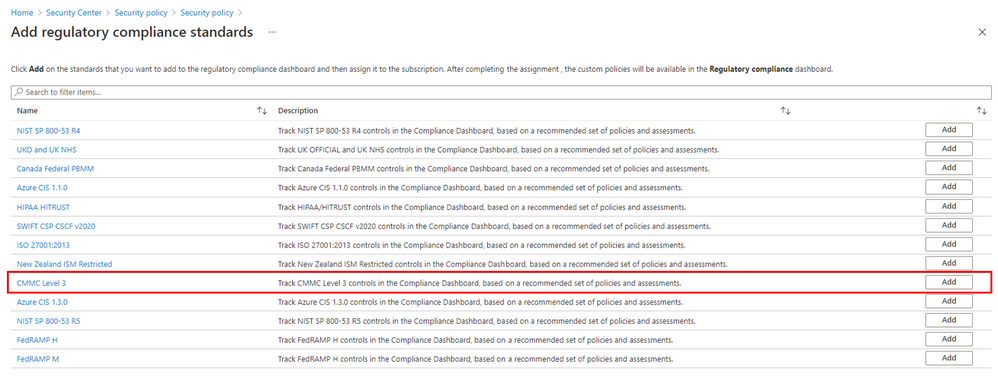
We recently added an Azure Policy Initiative that maps to CMMC Level 3 controls. This CMMC Level 3 Policy Initiative can be activated in Azure Security Center to quickly help you assess compliance with the control. Note that it is important to remember that there often is not a one-to-one or complete match between a control and one or more Azure Policies. As such, “Compliant” in Azure Policy refers only to the policy definitions themselves; this doesn't ensure you're fully compliant with all requirements of a control. In addition, the compliance standard includes controls that aren't addressed by any Azure Policy definitions at this time. Therefore, compliance in Azure Policy is only a partial view of your overall compliance status. The associations between compliance domains, controls, and Azure Policy definitions for this compliance standard may change over time. The CMMC Level 3 Initiative can be applied in Security Center’s Regulatory Compliance page.
Reporting your CMMC Compliance with Azure Security Center
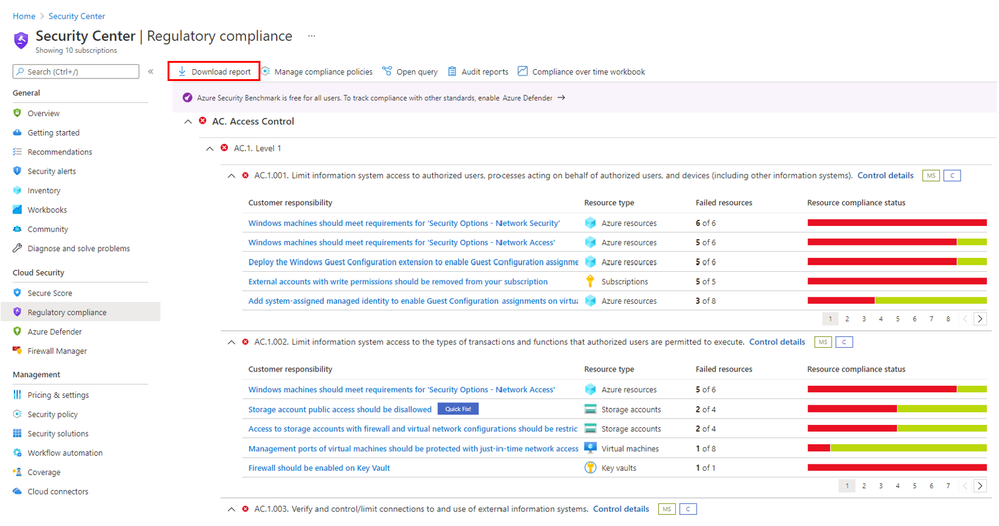
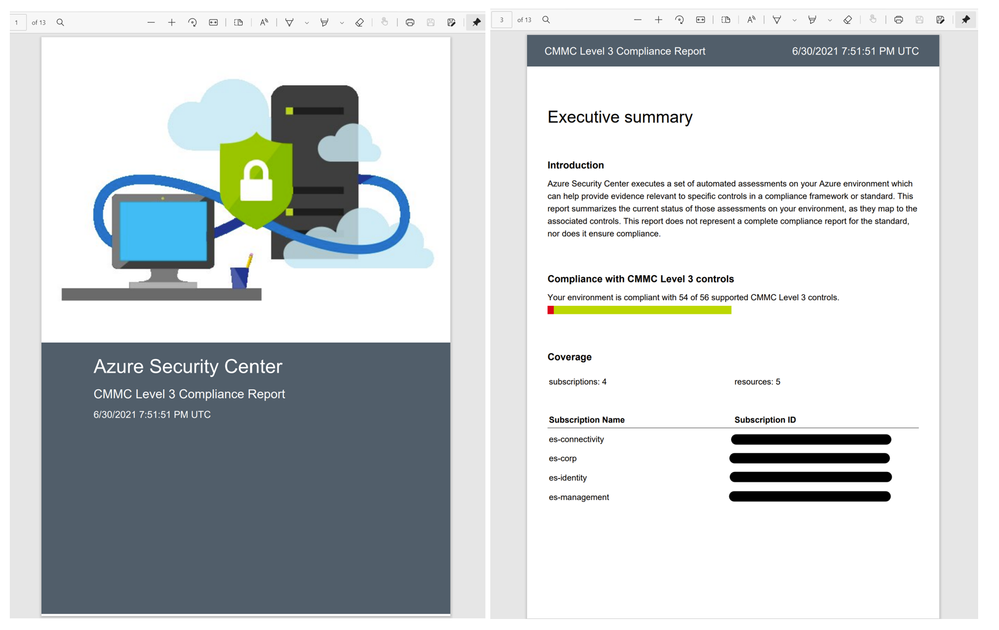
After deploying your landing zone, implementing policies, and configuring the CMMC Level 3 Initiative, you can leverage Security Center to help evaluate compliance with CMMC. In addition to the Azure Security Compliance dashboard for CMMC Level 3, you can generate downloadable reports, as indicated below, to share with relevant parties such as your Risk Team, Auditors, CSO, or Executives.
Below is a sample PDF report, but you can choose CSV format as well.
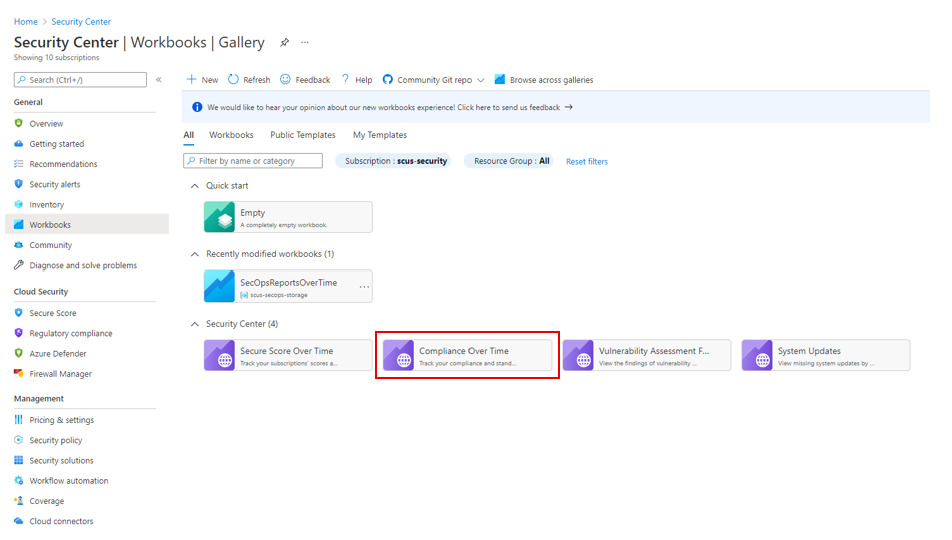
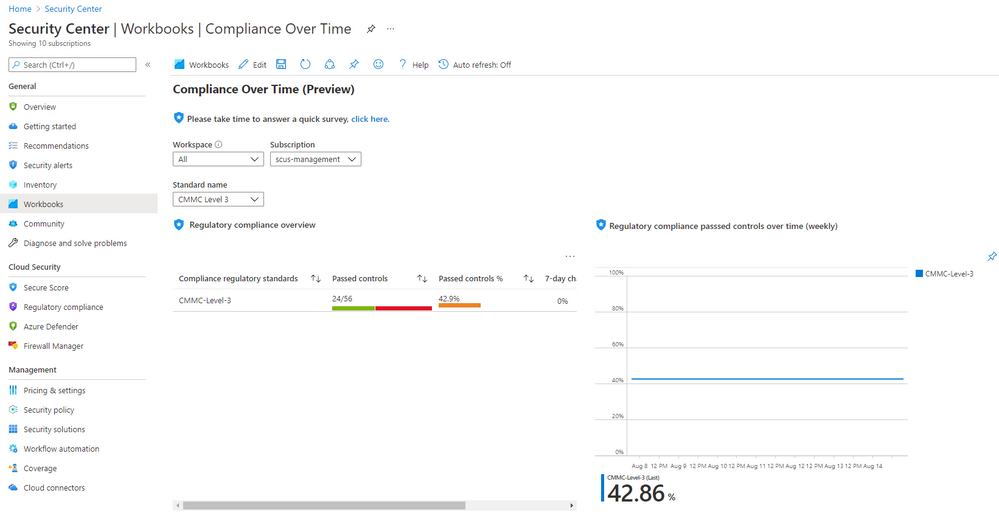
Security Center also has built-in workbooks that display compliance over time.
Summary
When used together, this is a great way to get your landing zone deployed (with a lot of the design and planning work done for you) and then apply, report, and visualize your CMMC Level 3 compliance. If you have any questions related to Azure Landing Zones or CMMC Level 3 policy mapping, please leave a comment below.
Special thanks to:
@RichardWakeman for collaborating on and reviewing this post
Posted at https://sl.advdat.com/2Y5BhlR