Microsoft is committed to endpoint management that helps organizations protect apps and devices across their platforms of choice. Apple devices, apps and operating systems continue to be critical components of an organization's endpoint estate. Today we are announcing Microsoft Endpoint Manager capabilities that support the changes announced by Apple at WWDC 2021 as well as additional functionality designed to help make it easy for users to do their best work on Apple devices while simplifying how IT administrators can help protect sensitive information and avoid getting in the way of user productivity.
Protecting data and user experiences with flexible controls for iOS/iPad
Microsoft Intune, as part of Microsoft Endpoint Manager, brings the controls needed to protect managed and unmanaged app data on iOS and iPad devices with application protection policies. , organizations can use Intune to apply policies that set copy and paste restrictions based on apps that are configured using open-in management controls to view company or personal documents.
Some organizations may choose to increase security by controlling connections to external sources, such as servers or paired devices. For example, they can disable a device connection to the Siri servers for translation (iOS/iPadOS 15+) and dictation (iOS/iPadOS 14.5+). When this restriction policy is applied, users will be prevented using the translation and dictation capabilities through Siri. Similarly, administrators can prevent users from automatically unlocking their devices running iOS/iPadOS 14.5+ with their Apple watch. With devices running iOS and iPadOS 14.2+, administrators can also prevent managed or unmanaged devices from pairing with other near-field communication (NFC) enabled devices.
Universal links simplify how users transition between web content and applications on iOS and iPad devices. To protect sensitive corporate data, Intune app protection policies can also be used to manage universal links to ensure your data is shared only with the applications you allow. Although not specifically associated with updates coming in iOS and iPadOS 15, with the October 2021 release (2110) of Microsoft Endpoint Manager, you will be able to customize the app protection policies of universal links in two ways. First, you will be able to designate universal link exemptions. Exemptions allow links found in corporate content or data to launch into unmanaged applications that your organization trusts. Second, you will be able to designate managed universal links. Managed links allow you to choose whether the universal link opens in the protected browser of your choice or in the application protected with app protection policies associated with the universal link. Combined, these features allow you to customize the data protection experience for universal links in your endpoint deployment.
For added protection, organization can use a device configuration in Intune to apply a profile to iOS and iPadOS managed devices running iOS and iPadOS 14.5 + that can restrict users from booting their devices into recovery mode with unpaired devices. Although off by default, this setting enables administrators to prevent the risk of an unpaired device or host computer to erase the device data to restore the operating system.
Zero Trust approach to endpoint security
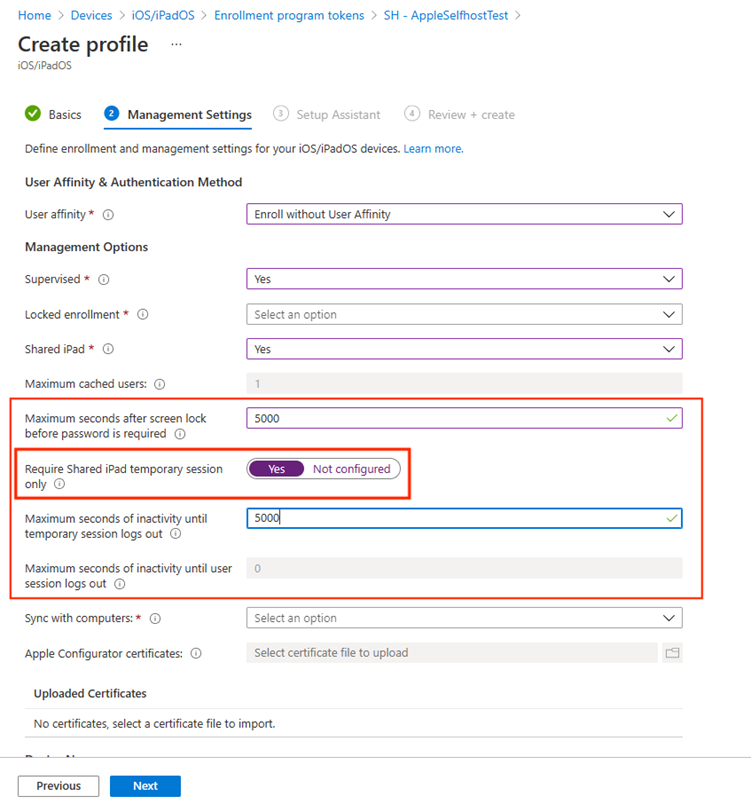
Frontline workers account for 80 percent of the entire global workforce, and just about everyone agrees that keeping these workers digitally connected is a highly strategic differentiator. On devices that are shared between workers on the frontline, Microsoft helps organization deliver simplified and secure experiences. Organizations can continue their journey to a Zero Trust security model by managing least privilege access for devices in Shared iPad mode. Using Microsoft Endpoint Manager, an administrator can accomplish this using following settings on devices running iPadOS 14.5 or newer:
- Require temporary session: Specify when a device can be accessed only by a guest user. Users will see the Guest Welcome pane and can't sign in with a Managed Apple ID.
- Set the log out time: Specify the maximum number of seconds of inactivity after which the temporary session or user session automatically signs out.
- Set screen lock timing: Specify the maximum number of seconds after the screen locks, before requiring the user to re-enter the device password (Available for iPadOS 13+).
To help you verify explicitly, on devices using Kerberos on Apple devices for user authentication, Microsoft is announcing the plan to introduce several enhancements to the Kerberos Single Sign-on extension, on both iOS/iPadOS and macOS devices. In the October release of Microsoft Endpoint Manager, administrators will be able to provide customizable help text to display to the user at sign-in, allow only managed apps to access and use the Kerberos credential, create an ordered list of preferred Key Distribution Centers for Kerberos traffic, and more. To learn more about the available settings that are configurable in Endpoint Manager today with Kerberos SSO extension, see iOS/iPadOS device feature settings in Microsoft Intune or macOS device feature settings in Microsoft Intune.
With the shift to remote and hybrid work, ensuring access to company resources from mobile devices became ever more important. Microsoft announced at Spring Ignite 2021 that we combined Microsoft Defender with Tunnel VPN into one Microsoft Defender for Endpoint app. Without making any changes to your Tunnel Gateway configuration, your users can connect to Tunnel and see connection status in Defender for Endpoint. If you’re also using Defender for Endpoint to provide web protection for your iOS devices, your users will continue help to see the threat level of their device in the same app, and administrators can manage the Tunnel and Defender setting for one app in Microsoft Endpoint Manager. The Defender for Endpoint app with Tunnel functionality for iOS and iPadOS devices will be available in public preview in the coming weeks.
Also available with managed devices running macOS 12 is the ability for organizations to use Endpoint Manager to help prevent accidental data loss by disabling the reset option. By configuring this setting, organizations can block users from erasing all content and settings on their device.
Settings catalog in Microsoft Endpoint Manager simplifies the way to create policies and configure settings for managed devices by listing out the settings available all in one place. We recently updated the settings catalog with Defender for Endpoint for macOS. In the past, a property list (plist) file needed to be used to configure settings for Microsoft Defender for Endpoint. Now available to customers in public preview, we added eight settings to manage Microsoft Defender for Endpoint on macOS under antivirus, cloud delivered protection preferences, user interface preference and a new network protection category. For information about these settings, see Set preferences for Microsoft Defender for Endpoint on macOS.
We recently released the Setup Assistant for Modern Authentication for iOS, iPadOS and macOS. This changed now enables users to authenticate (including multi factor authentication) with their work account before enrolling their corporate devices. Administrators also have more confidence in the increased security that comes with identity-based authentication.
One of the most common requests by customers is to make PKG app deployment formats easier to use as well as support non-PKG apps. In the August edition of What’s New in Endpoint Manager we announced the that administrators can now review and edit the logic that Intune uses to detect the successful installation of apps on a mac device before deployment. This means that if any issues are detected, they can be addressed in advance which can result in a reduced number of support cases in this area and easier app deployments. Be sure to view this short video demo on how to use the new capability included here for your convenience. Stay tuned for more updates in future releases that will broaden our support for additional app formats.
Looking to the future - experience matters
Apple announced declarative device management (DDM) that focuses on bringing policy management to the device rather than through the server. By doing more on the device, it is anticipated that DDM will result in more autonomous devices with less reliance on the server for such things as policy delivery or device compliance. Microsoft is excited about this approach as it may introduce improved performance and experiences for devices enrolled in Intune by minimizing the number of server check-ins. We are exploring how best to integrate DDM to help increase reliability and efficiency of policy delivery. It is important to note that existing policies your organization has in place will not be affected by Apple’s introduction of DDM. Intune will continue to maintain support for the current device management model.
Apple also announced several updates to device enrollment including an account-driven user enrollment experience for personally owned or iOS and iPadOS 15+ and changes to managing software updates on device with macOS 12+.
Account-driven enrollment includes the display of user’s managed Apple ID in the Settings app on devices running iOS 15+. Microsoft is excited about this update as we anticipate it will introduce additional management and capabilities for devices enrolled in Intune. We are actively exploring how best to integrate this change and further simplify the enrollment experience for both users and administrators. In the meantime, the current enrollment flows will continue to function as they do today.
By using Intune to manage software updates, IT administrators will soon be able to schedule, configure, and send software update policies to macOS devices that are managed and/or enrolled with device enrollment program (DEP), now known as Automated Device Enrollment (ADE), as well as macOS devices with the Intel chip or with Apple silicon. To provide a consistent experience across the endpoint estate and help simplify support and other endpoint workflows, a new setting available for devices running macOS 12 will allow IT administrators to specify the maximum number of times a use can defer an update, after which a forced update will occur on the device.
Additionally, administrators will be able manage the visibility of available updates. This way they can help control user experiences and deployments to be ready when they are. For example, administrators can specify the number of days a major OS update such as macOS 12 is visible to end users. Our plans include the ability for administrators to define the number of days to defer major and minor OS updates on iOS 11.3 and non-OS updates on 11+ in Intune. We’ll share more details for future releases when the details are available.
To summarize, Microsoft is very excited to announce the key capabilities that will be available upon the release of Apple iOS and iPadOS 15 and macOS 12 as well as other developments in Microsoft Endpoint Manager designed to deliver secure data, app and endpoint experiences across the Apple ecosystem. We continue to invest in areas of cloud connected, unified endpoint management that adapt to the evolution of customer needs, the technology landscape and the way we work.
As always, we want to hear from you! Tweet your feedback using the hashtag #MEMpowered. If you have questions about this article, add a comment below or reach out to @IntuneSuppTeam on Twitter. Feel free to add an idea for a new feature to UserVoice and keep up with ongoing developments on Endpoint Manager by following the Microsoft Endpoint Manager Blog and @MSIntune on Twitter.
Posted at https://sl.advdat.com/2YWGkFv