The threat landscape has evolved over the past few years. Hackers are “shifting-left,” compromising upstream dependencies and engineering systems. These advanced attacks can impact entire development environments and software supply chains. One recent example occurred at a software vendor where an attacker targeted their developer workflow and software supply chain. After gaining access, the attacker uploaded a new image into thousands of builds that scanned their software supply chain—extracting secrets/credentials and widening the breach. This attack exemplifies how it’s no longer enough to just integrate security within the DevOps workflow, now you must harden and secure the workflow itself!
So, how do you secure your upstream development environments?
Kick it off by securing all developer machines and ensuring that your developers interact with non-trusted code in a secure manner. These steps help prevent malicious code from executing on developer machines and prevent hackers from using developer machines to act as a "jump-box" to further systems.
GitHub Codespaces is a solution where your developers can securely interact with non-trusted code inside a sandbox environment. This cloud-powered development environment is available anywhere, on any device. Going further, it’s never been simpler to manage user permissions, store encrypted secrets in the right places, and implement GPG verification, so that commits are verified and made only by trusted users. And it’s fast too. Your team can go from zero to a functioning development environment in less than 10 seconds! Developers can spin off new Codespaces for parallel workstreams with no overhead. The solution is flexible and efficient while also providing security, compliance, and productivity enhancements for your organization.
Along with developer machines, you’ll also need to secure your DevOps workflows. GitHub Actions helps your development teams easily create secure and automated workflows to build, test, package, release, and deploy apps to Azure or any other cloud. Azure provides a rich set of GitHub Actions integrations that help you adopt an “everything as-code” DevOps model. In this model, compliance and security policies, build and release pipelines, etc. are written “as code,” enabling continuous improvement, better re-use, and greater transparency.
It’s now common for hackers to target development environments, use discovered credentials to tamper with source code, and inject malicious code. Compounding this risk is the fact that your development teams must store their Azure service principal secrets in GitHub, which is both redundant and extremely risky. At Microsoft Ignite 2021, I’m excited to announce the preview of capabilities that enable developers to secure their deployments to Azure without requiring them to store long-term credentials in GitHub!
Remove credentials from developer environments with new Azure and GitHub integrations
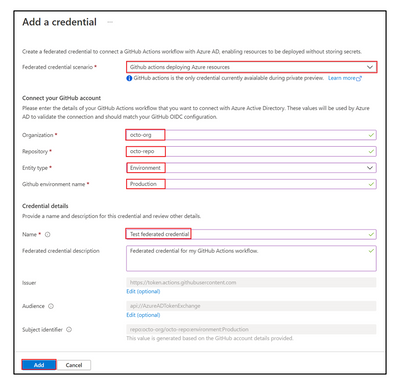
Removing long-lived, Azure credentials from the development environment is a key strategy to reduce vulnerabilities that hackers can easily exploit. You can now deploy from your GitHub repo to Azure without creating, storing, or managing credentials for Azure AD applications. This uses the Azure AD workload identity federation capability which is now in public preview. The new capabilities alleviate the need for managing Azure service principal secrets and other long-lived cloud credentials in the GitHub secret store. With this integration, you can manage all cloud resources access securely in Azure. These capabilities also minimize the chances of service downtime due to expired credentials in GitHub.
Setting up OpenID Connect (OIDC) integration with Azure AD and GitHub Actions
To set up a secured GitHub Actions workflow using OpenID Connect integration with Azure AD you'll need:
- An Active Directory application with a service principal that has contributor access to your subscription
- An Active Directory application configured with a federated credential to trust tokens issued by GitHub Actions to your GitHub repository. You can configure this in the Azure portal or with Microsoft Graph REST APIs
- A GitHub Actions workflow that requests GitHub issue tokens to the workflow and uses the azure/login@v1.4.0 action
To learn more about how to set up the integration, check out the documentation.
Start building secure apps with GitHub and Azure
With deep integrations between GitHub and Azure, the Microsoft DevSecOps solution is the complete software development solution that empowers your development teams to securely deliver cloud-native apps at DevOps speed! This solution enables you to write more secure code, respond quickly to vulnerabilities in your software supply chain, adopt best practices to harden your development environments, and foster collaboration between your developers and security teams.
For more information on integrating security into your development lifecycle and hardening your DevOps workflows, check out our e-book.
Posted at https://sl.advdat.com/3mBAbbe