Patching can be a struggle for a lot of organizations. However, it is one of the most basic security tasks that security defenders must ensure happens regularly. If you’re still manually patching your servers, you need to look into Azure Arc and Azure Automation to automate this.
Azure Arc extends management from Azure to on-prem or 3rd party cloud infrastructure. By installing the Azure Arc agent on an on-prem or 3rd party cloud server, it allows you to manage and gain insight on that server in your Azure tenant along side your other Azure servers.
Azure automation is an extremely powerful tool. In this blog, I will go over how to use it to automate patching but there are a lot more things Azure automation can do.
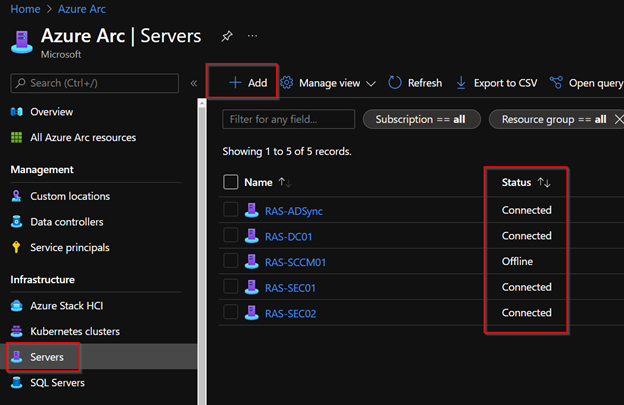
The first thing you need to do is install the Arc agent on your servers. You can do this via a script either manually or deployed through management. Go to Azure Arc --> Servers --> Add.
As you’ll notice in the screenshot, I have a few servers onboarded already. Here you can see the status of each server. These are on-prem servers that are not in Azure. As I was writing this blog, I noticed one of my servers was offline signaling that there may be some issues. This can be very helpful for admins.
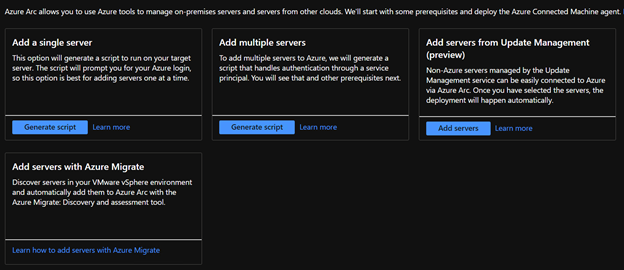
There are many ways to onboard servers. For demo purposes, we’ll use a single server script. Multi-server scripts require an Azure service principal.
Walk through the script generation by selecting the Resource group you want your Arc servers to go into and the region. The region will be important later when we create the automation account. On the Tags page, you can choose to tag your assets. This may be important when you’re managing multiple datacenters, servers, locations, etc… You can scope your automation to different tags.
Finally, download the script. Transfer it to your server and run it to onboard the server to Arc. If done correctly, the server should appear in seconds. You should also see the Azure Connected Machine Agent under the installed programs.
If you do not have a Log Analytics Workspace create, you will need to create one. It is important to note that servers can be linked to only ONE Log Analytics Workspace. It is best practice to have one workspace for all of your security workloads. For example, if you have a Log Analytics Workspace for Azure Sentinel, I would use this same workspace for your Arc servers and automation unless you have specific compliance or geographic restrictions.
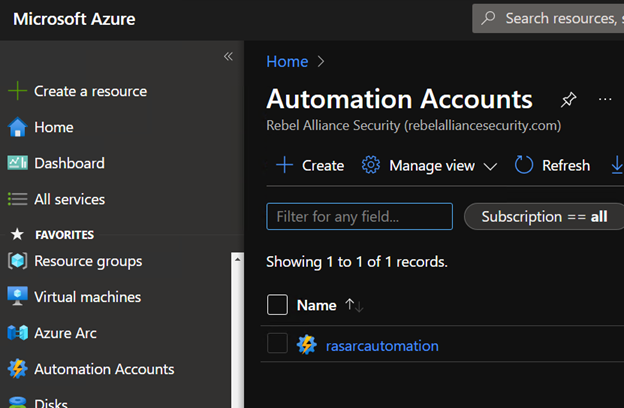
Once you have your Log Analytics Workspace created, you’ll need to create the automation account. Go to Automation Accounts and click “Create.”
Select the Resource Group and Region for your automation account. VERY IMPORTANT: Your automation account must be in the correct linked region to your Log Analytics Workspace. For example, if your Log Analytics Workspace is in US East, your Azure Automation Account must be in US East 2. Check this page to find out what the correct linked region is prior to creating your automation account.
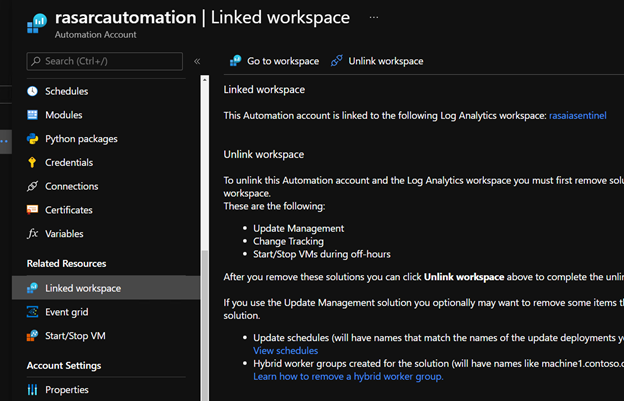
For demo purposes, I selected System Assigned Identity for my automation account. Once your account is created, the first thing you need to do is link the workspace. Click on the account and navigate to “Linked Workspace” and select your workspace with your Arc servers.
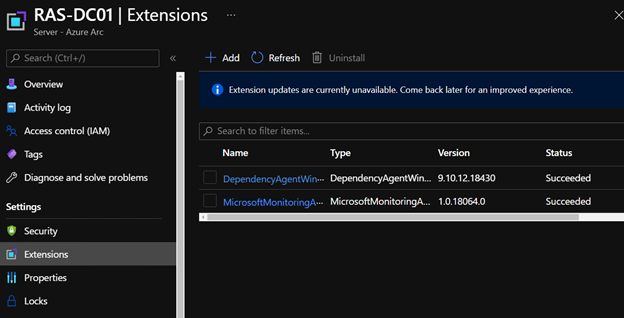
Next, we need to make sure the Log Analytics VM extension is installed on Arc-enabled servers. This will allow the servers to show up in the Update Management tab of the Automation account. There are multiple ways to do this but the easiest is to deploy it through Azure Arc. You can review deployment options in this document. Go back to Azure Arc and select one of the servers. Navigate to “Extensions” and make sure the DependencyAgentWindows and the MicrosoftMonitoringAgent are installed successfully.
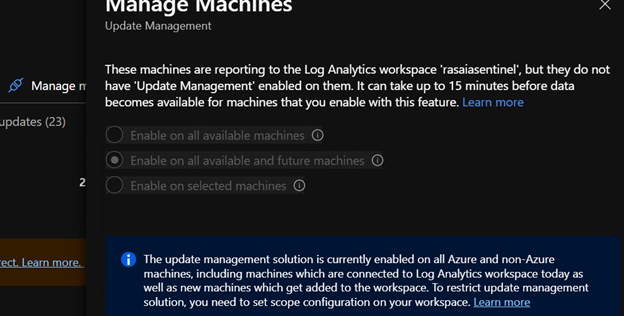
Now, to enable Update Management, go back to your Automation Account and navigate to Update Management. Click on “Manage Machines” and enable it on some, all, or even all future machines in the Log Analytics Workspace.
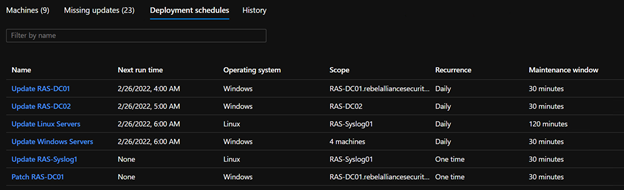
Your machines should show up on the list. Some may be compliant. Some may not be. This depends on your Azure policy assigned to the machine (which we won’t get into on this blog). However, the basic compliance is based on your critical updates. To update your machines, you’ll need to create a deployment schedule. Click on “Schedule Update Deployment.”
You can get very granular with your deployment down to a single machine. Select your scope, recurrence, and maintenance window for your schedule.
Now, sit back and enjoy seeing your servers patched without having to do anything. You can onboard Azure servers as well if they live in the same Log Analytics Workspace. Hopefully this gives organizations an idea on how to use Azure Arc and make patching a non-issue!