The MITRE ATT&CK framework has been around for years. Today, it’s commonly used by organizations as a tool for understanding current security coverage and determining how to improve it. When looking at the constantly changing threat landscape, it’s essential to understand our own blind spots and how well we’re covered against specific threats.
The analytic rules -
Microsoft Sentinel’s bread-and-butter for defending organizations against threats is our analytic rules.
Analytics rules search for specific events, or sets of events, across your organization's data sources, alert you when certain event thresholds or conditions are reached, generate incidents for your SOC to triage and investigate, and respond to threats with automated tracking and remediation processes.
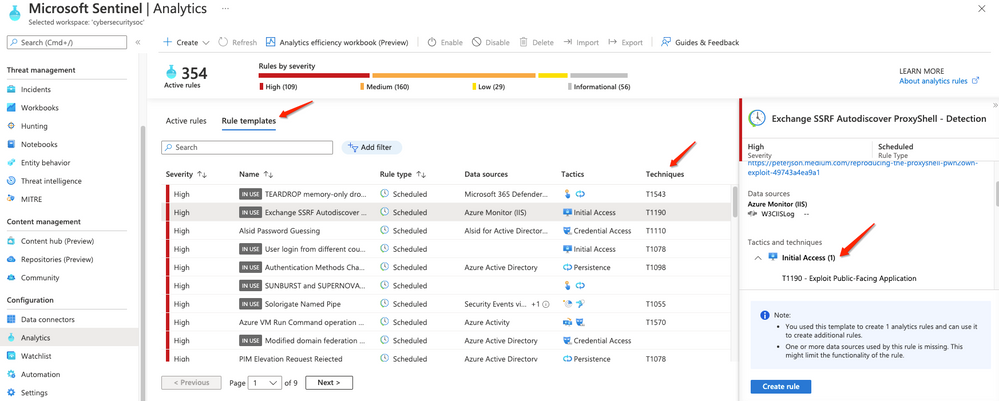
You can use our rich set of out-of-the-box detections, tagged with the relevant MITRE techniques and tactics, or create your own.
(analytics templates)
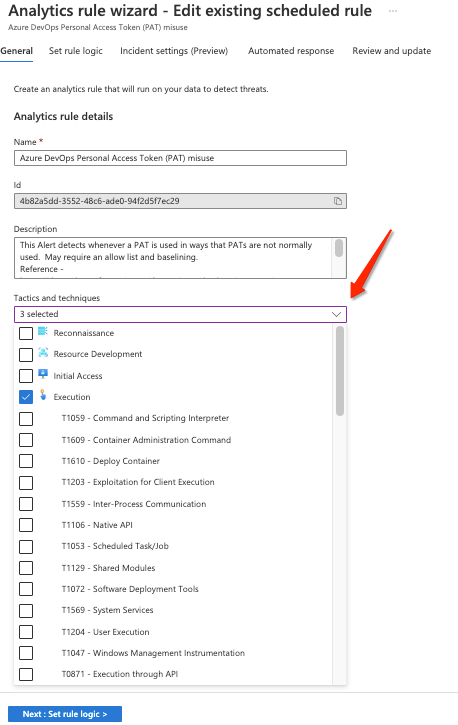
When creating a custom detection in an analytics rule, tag it with the relevant MITRE tactics and techniques, which you’ll later use to determine the MITRE ATT&CK framework coverage. For example:
(Rule creation wizard)
Note: Tagging analytics rules with incorrect tactics or techniques will result with false coverage indications.
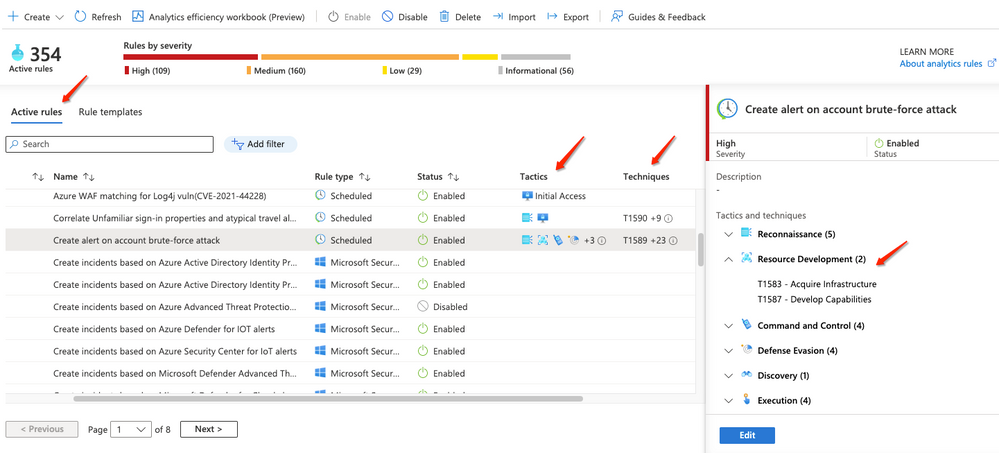
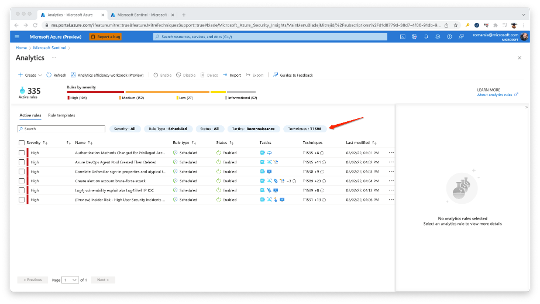
Microsoft Sentinel displays the tactics and techniques as a part of the analytics view so you can monitor and filter by them.
(Analytics rule view)
When analytics rules are tagged with MITRE ATT&CK tactics and techniques, any new incidents created from those tagged rules will also have the same tactics and techniques associated.
The incidents
When selecting an incident in Microsoft Sentinel, a pane opens on the right where you can see details about the selected incident. For example, view the incident’s severity, a summary of the number of entities involved, the raw events that triggered this incident, the incident’s unique ID, and any mapped MITRE ATT&CK tactics or techniques.
Tag your rules correctly so that the SOC analyst viewing the incidents will get additional context on the attack, based on the correct MITRE tactics and techniques.
(Incident side panel)
The hunting queries
Microsoft Sentinel has powerful hunting search and query tools to hunt for security threats across your organization's data sources.
To help security analysts proactively look for new anomalies that weren't detected by your security apps, or even by your scheduled analytics rules, Microsoft Sentinel's built-in hunting queries guide you in asking the right questions and find issues in the data you already have on your network.
Each hunting query is associated with a MITRE tactic and technique.
(Hunting view)
The MITRE view
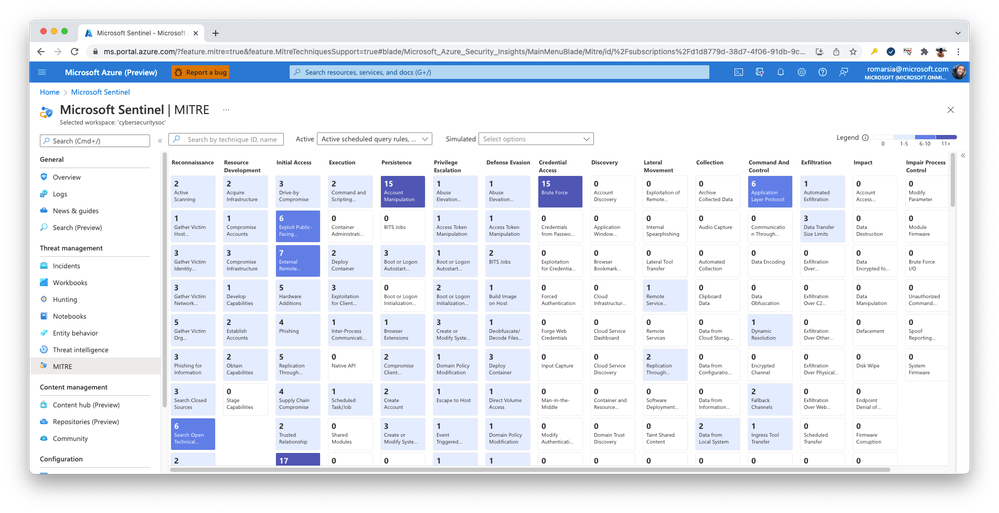
Now, after tagging all your analytics rules and hunting queries correctly, enjoy the full power of the MITRE view in Microsoft Sentinel.
In the Threat management menu on the left, select MITRE.
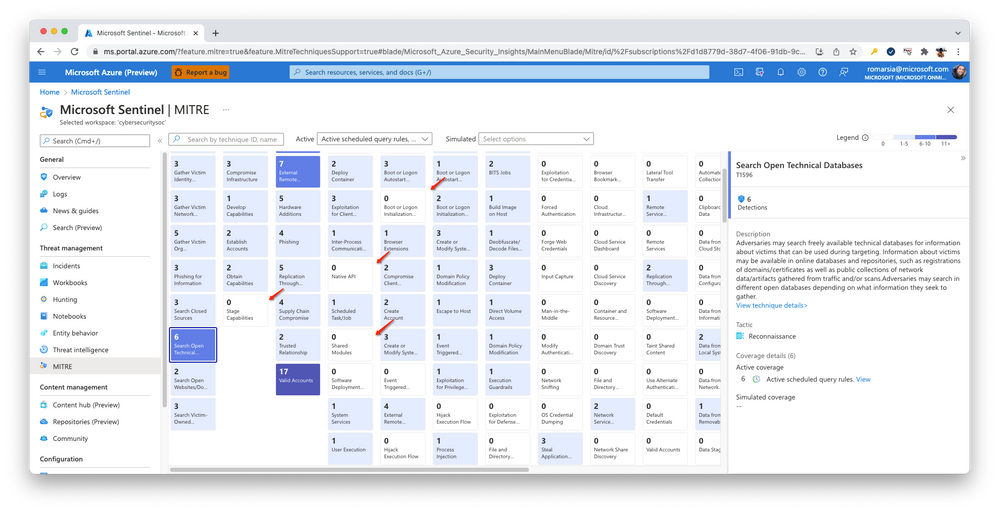
The MITRE view displays each tactic in a column, and each technique in tiles in those columns.
The color of each tile is determined by the number of detections associated with the technique, as described in the legend at the top right.
By default, both active scheduled query rules and NRT (Near Real Time) rules are indicated in the coverage matrix.
Disabled rules are not represented in the MITRE view, as disabled rules don’t provide any protection against threats.
In the MITRE view, select a tile.
On the right, you’ll see the name, tactic, and the full description of the technique, as described in the MITRE documentation.
To jump over into the full description in the MITRE documentation, select View technique details.
For the example shown above, we should expect to see 6-10 detections, based on the tile’s color coding. In fact, the selected technique in this example (T1596) has 6 detections. View details for these detections in the Analytics view by selecting the View link under Active coverage.
Once there, we see that the active rules displayed are filtered for the T1596 (Search Open Technical Databases) technique.
How can I leverage the MITRE view to improve security coverage?
After viewing your current security coverage in the MITRE view, we can see specifically where you're covered – and more importantly, where you are not covered.
Note that the relevance of each technique varies between organizations.
For example, if your organization knows that it is targeted by a specific attack group, the techniques associated with that attack group are more relevant to you. In this case, you may want to add new detections to block additional techniques or strengthen existing ones.
To improve your organization’s security coverage, use the MITRE view’s simulation ability to see what Microsoft Sentinel has to offer, out-of-the-box.
In the Simulated dropdown menu, select Analytics rule templates to see how enabling templates will improve the overall protection.
Coverage is not all
The MITRE view provides us with a way to determine the security coverage, but it doesn’t give us the full picture.
The MITRE view considers all detections as equals, and this isn’t always the case. Having many detections, even on all the techniques, doesn’t always mean that the organization is well-covered.
The MITRE ATT&CK framework is only one part of assessing risk. You also have to look at coverage, asset discovery, external risk, vulnerability management, defense in depth, and other ways to look at maturity of your cyber security practice.
On the other hand, using the MITRE view as a part of a process for risk assessment and prioritization can result with an organization that can dynamically adjust and change according to threats.
Posted at https://sl.advdat.com/35vf2ckhttps://sl.advdat.com/35vf2ck