Special thanks to @Amit-Lal, Microsoft for collaborating and co-writing this technical article with me.
In this blog post we will show how you can use the SOAR capabilities of Sentinel with SAP by using Azure playbooks/Logic Apps to automatically take remediation actions in a SAP S/4HANA/ECC/BW system.
Firstly, some background: organizations around the world rely on SAP systems and their applications to handle massive amounts of business-critical data. It has been notoriously challenging to detect these threats to SAP applications, while the consequences of an undetected threat in a SAP application can be extremely serious.
This difficulty in detection stems - in part - from the complex internal nature of SAP systems, as well as the fact that these systems usually have lots of cross-connections between different applications.
Continuous Threat Monitoring for SAP in Microsoft Sentinel
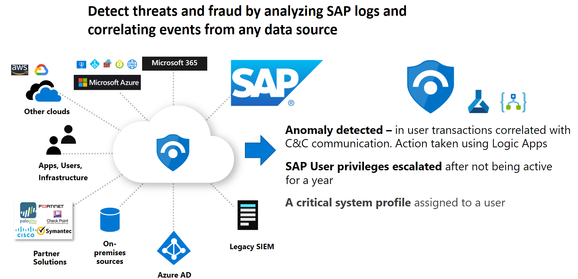
The Continuous Threat Monitoring solution for SAP in Microsoft Sentinel enables you to monitor your SAP environment and helps you with cross-correlating logs from numerous systems with your SAP logs. With the Microsoft Sentinel SAP connector you can monitor your SAP systems for sophisticated threats within the business and application layers. The connector uses a docker container, which pulls the data from SAP and then sends it through to Microsoft Sentinel.
For a detailed description on how to deploy the SAP continuous threat monitoring with Sentinel, see Deploy SAP continuous threat monitoring | Microsoft Docs
By deploying the data connector, we can now import the SAP logs into Sentinel and correlate the logs with other data and analyze and hunt the logs for emerging threats. Install the SAP solution security content to gain insight into your organization's SAP environment and improve any related security operation capabilities. For a complete overview of what is included in the Sentinel SAP solution content, see Microsoft Sentinel SAP solution - security content reference | Microsoft Docs.
Microsoft Sentinel also contains a Security Orchestration and Automated Response (SOAR) capability which will help you respond to incidents rapidly if they are detected in your SAP application:
SOAR with SAP overview & use case
We are going to focus on a practical use case example for automating SAP actions as a response to an incident in Sentinel.
Use case: Block the SAP dialog or RFC user after suspicious user-incident
- The SOC team is alerted of a suspicious atypical travel alert.
- After triaging the incident, the SOC team decides to block the user's access to sensitive environments. One of these sensitive environments is the SAP system to which the user can't have access anymore.
- The SOC team runs playbooks for these automatic remediations and one of the playbooks is the ‘BlockSAPUser’-playbook.
The goal here is to block the SAP dialog or RFC user access by locking the dialog or RFC user accessing SAP S/4HANA or NetWeaver system and do it in an automated way.
Getting Started
For this blog post we will make use of the data gateway to leverage the SOAR capabilities from Sentinel on SAP.
The gateway makes it possible to have a secure data transfer between data sources and a service in the cloud. The data gateway should be installed on a Windows Server. It is possible to use a dedicated machine or install it on the machine on which SAP is running, but you must ensure that both the VMs can communicate to each other over the private IPs.
- For more information on the installation and prerequisites for this data gateway, please visit Install on-premises data gateway - Azure Logic Apps | Microsoft Docs
- You can download the gateway via Download On-premises data gateway from Official Microsoft Download Center
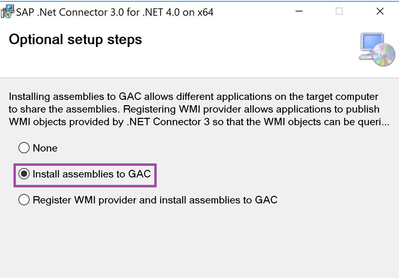
When you have installed the data gateway, you will also need to install the SAP Connector for Microsoft .NET 3.0 on the same machine as the data gateway. The SAP Connector for Microsoft .NET 3.0 will allow us to use BAPIs and remote-enabled function modules in a .NET application. You can download the SAP connector via Software Downloads - SAP ONE Support Launchpad
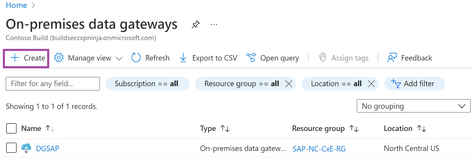
For our final preparatory step, we will have to create the gateway cloud service to finalize the handshake between the cloud services and the data gateway.
More information on creating the Azure gateway resource can be found at Access data sources on premises - Azure Logic Apps | Microsoft Docs
SAP on Azure -Architecture Reference with Azure resources and workflow

High level sequence of flow
- SAP Users/RFC User(s) connected from SAP system using SAP RFC /SOAP to Docker container running on Azure (Considering SAP running on-prem or Azure or any other hyperscalers like AWS or GCP as depicted above in Architecture.)
- Microsoft Sentinel detects & triggers an atypical travel Alert/incident if any specific SAP user breaches or run unauthorized transaction or Interface in the SAP system.
- Azure Logic Apps connected with Microsoft Sentinel and data Gateway (using SAP connector) triggers the SAP BAPI Lock function for that specific SAP user.
- This BAPI function triggered by Logic Apps connected to the SAP system locks the SAP user automatically. Note that you can send email via Logic Apps to the SOC manger to alert for this SAP user locked (an optional step can be added for a SOC alert mechanism setup).
Playbook
In this use case a suspicious user will be blocked from accessing the SAP environment.
The SOC team has been notified of an ‘Atypical travel’ alert in Sentinel. After thorough investigations they decide to block the user entity from accessing the SAP environment and use the “Run playbook” action to start automatic remediation.
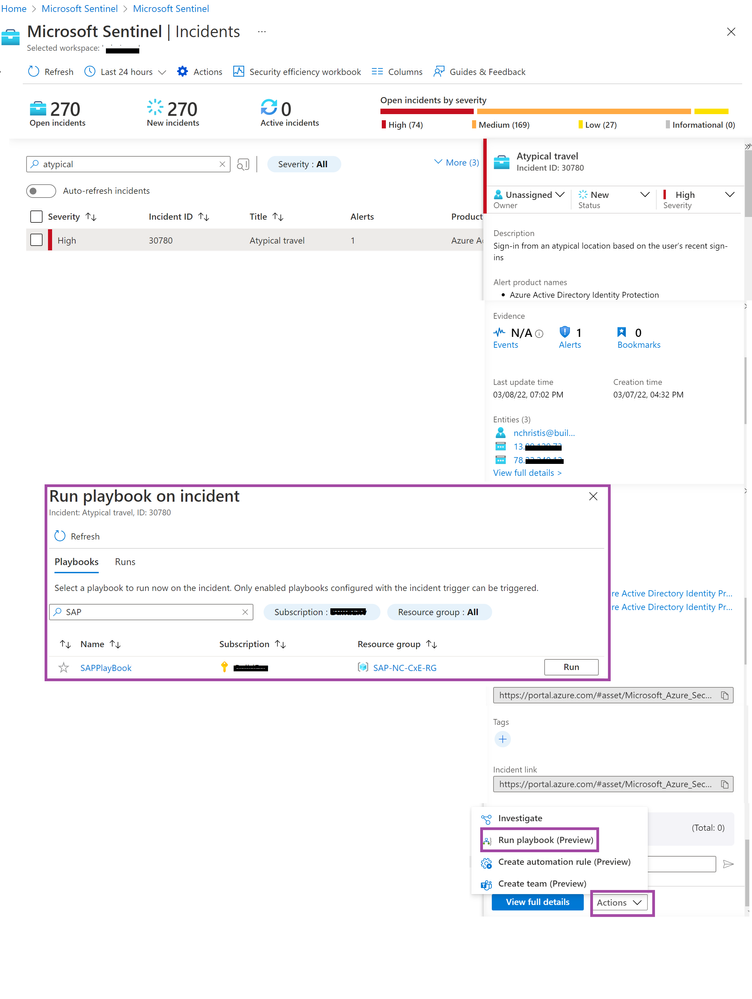
This playbook will use the Microsoft Sentinel incident as a trigger, so that you can use it as an automatic action on an incident.
In the playbook the ‘Create stateful session’ action from the SAP connector (see: SAP - Connectors | Microsoft Docs) is used to make the connection with SAP.
When the connection has been made, extract the user entity from the Sentinel incident and use ‘BAPI - Call method’ to block the user in SAP. For more information visit Connect to SAP systems - Azure Logic Apps | Microsoft Docs

When the SAP user ‘nchristis’ tries to subsequently logon to the SAP S/4HANA system, she cannot access the system since she is locked out:
More complex use cases (e.g. with extra steps for approval from the SOC manager via teams or delete the user account instead of blocking it) are possible and we encourage you to try it out on your own!
Posted at https://sl.advdat.com/3JcTPmIhttps://sl.advdat.com/3JcTPmI