Disclaimer
This document is not meant to replace any official documentation, including those found at docs.microsoft.com. Those documents are continually updated and maintained by Microsoft Corporation. If there is a discrepancy between this document and what you find in the Compliance User Interface (UI) or inside of a reference in docs.microsoft.com, you should always defer to that official documentation and contact your Microsoft Account team as needed. Links to the docs.microsoft.com data will be referenced both in the document steps as well as in the appendix.
All of the following steps should be done with test data, and where possible, testing should be performed in a test environment. Testing should never be performed against production data.
Target Audience
The Information Protection section of this blog series is aimed at Security and Compliance officers who need to properly label data, encrypt it where needed.
Document Scope
This document is meant to guide an administrator who is “net new” to Microsoft E5 Compliance through.
We will be running PowerShell scripts to allow the Secirity and Compliance portal to access labeling in SharePoint Sites and Teams Containers.
It is presumed that you already have a Sensitive Information Type that you want to use in your Information Protection policy. For the purposes of this document, I will use a copy of the U.S. Social Security Number (SSN) called “U.S. SSN – Numbers Only” that I created in Part 1 of this blog series.
Out-of-Scope
This document does not cover any other aspect of Microsoft E5 Compliance, including:
- Sensitive Information Types
- Exact Data Matching
- Data Protection Loss (DLP) for Exchange, OneDrive, Devices
- Microsoft Cloud App Security (MCAS)
- Records Management (retention and disposal)
- Overview of Advanced eDiscovery (AeD)
- Reports and Analytics available in of Advanced eDiscovery (AeD)
- Insider Risk Management
- Privacy Management
It is presumed that you have a pre-existing of understanding of what Microsoft E5 Compliance does and how to navigate the User Interface (UI).
It is also presumed you are using an existing Information Types (SIT) or a Exact Data Match (EDM) you have created for your testing.
We will not be working with pre-existing Teams sites.
At this stage, we will not be creating, publishing or adding labels to a SharePoint Site or Teams Containr. That will be done in Part 2b of this blog series “Adding a Sensitivity Label to a Container and/or Site”
Overview of Document
- We will be running PowerShell scripts to allow the Secirity and Compliance portal to access labeling in SharePoint Sites and Teams Containers.
Use Case
Create a Sensitivity Label and apply it to a Microsoft Team. This will apply the protection of a Sensitivity Label to protect the files within a Microsoft Team.
Definitions
- Sensitivity Label – a metadata tag
- Publish Label – making the metadata tag available to your tenant
Notes
- Containers (in SharePoint) are a gate keeper for access to files inside SharePoint/Teams sites
- Container labels do not apply labels to objects inside the container (ex. PPT and Word docs do not receive the label of the Container)
- When there is a mismatch of the label of a container versus that of a file inside the container, then this can be audited.
- The application of a sensitivity label at the Team container level prevents inappropriate / external team members from being added to the Team. This prevents oversharing from occurring in the first place.
- Privacy labels (Private, org-wide & public). These Sensitivity Labels are linked to the corresponding setting in the Container/Site configuration.
- Private – data stays inside a certain group of users within the organization
- Org-wide – data stays inside the organization
- Public – data available for access outside the organization
Pre-requisites
- Create a Sensitive Information Type (SIT) in Part 1 OR an Exact Data Match (EDM) in Part 1a of this blog series.
Adding the ability to label Containers and Sites
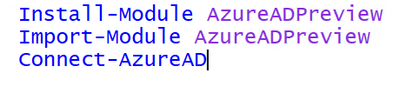
- On a VM connected to your AAD test tenant, run the following Powershell commands in Powershell_ISE with elevated rights:
a. Install-Module AzureADPreview
b. Import-Module AzureADPreview
c. Connect-AzureAD (this last command will ask for an administrative account
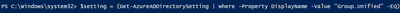
- Next run these following commands:
a. $setting = (Get-AzureADDirectorySetting | where -Property DisplayName -Value "Group.Unified" -EQ)
b. $template = Get-AzureADDirectorySettingTemplate -Id 62375ab9-6b52-47ed-826b-58e47e0e304b
c. $setting = $template.CreateDirectorySetting()
d. note - you might need to run these individually as compared to being part of PS script
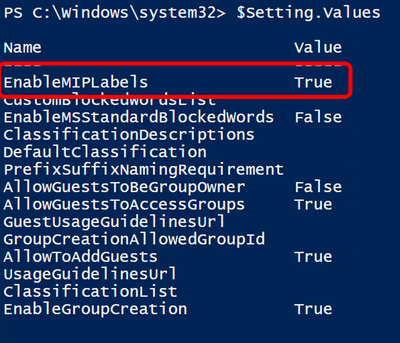
- Verify that the settings have been updated.
a. In a Command Prompt, check your settings with this command. It should look like the following with 3 Falses at the top and then 3 Trues at the bottom.
b. $Setting.Values
- Enable the MIP Labels (this is the top value above.
a. $Setting["EnableMIPLabels"] = "True
- Verify your settings have changed with this command by rerunning the command from above
a. $Setting.Values
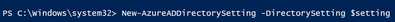
- Save the changes to AAD with the following command line:
a. New-AzureADDirectorySetting -DirectorySetting $setting
- Install Exchange module (if needed)
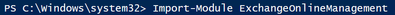
a. Install-Module ExchangeOnlineManagement
- Next import the ExchangeOnlineManagement. Run this PowerShell command
a. Import-Module ExchangeOnlineManagement
b. Note – you will need to allow for scripts to be run.
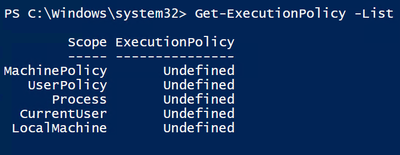
- This Powershell script will tell you if you can execute the Import-Module policy above
a. Get-ExecutionPolicy -List
- This PowerShell script will allow you to run the Import-Module
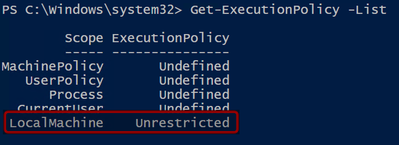
a. Set-ExecutionPolicy Unrestricted
- Run this Powershell script again to verify that the Local Machine has changed to Unrestricted”
a. Get-ExecutionPolicy -List
b. Note – documentation on the Get0ExecutionPolicy PowerShell script is in the Appendix and Links section below.
- Run this Powershell script to connect your IP session. You will need your administrator account name.
a. Connect-IPPSSession -UserPrincipalName username UPN. <UPN> is your account in user principal name format (ex admin@companyx.com )
- You will see this message indicating the PowerShell script is running.
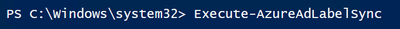
- The last step is to execute the following PowerShell script to synchronize your labels so they can be applied to SharePoint and Teams Grops and Sites.
a. Execute-AzureAdLabelSync
- You can now create and publish our Sensitivity Labels. Proceed to Part 2b of this blog series “Adding a Sensitivity Label to a Container and/or Site”
Appendix and Links
Posted at https://sl.advdat.com/364tFUghttps://sl.advdat.com/364tFUg