Overview:
We do receive customers request on how they can restrict Sql DBA/Admin azure users from enabling Azure defender on the resource level. In this blog article, we are going to explain how to archive this through Azure Access Control and Azure built-in role.
Solution:
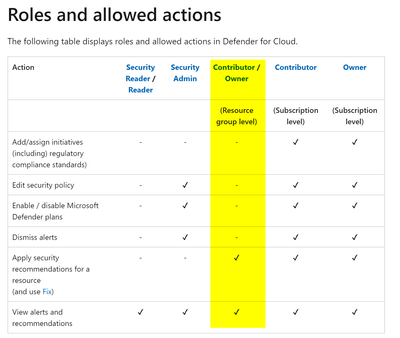
The owner/contributor roles can configure the Azure defender on the subscription and resource level, however this contains excessive permissions. To enable ‘Defender for SQL’ on the resource level, the ‘securityAlertPolicies’ permission must be allowed in a role. Depending on the type of Sql resource you have, there are different 'securityAlertPolicies' permissions to choose from. Below screenshot is what you get when creating a custom role (RBAC):
Therefore, in order to restrict users from enabling ‘Defender for SQL’ on resource level, you must use a build-in role that doesn’t have ‘securityAlertPolicies’ permission or create a custom role. Azure already has built-in roles that can be used to achieve this purpose, like: ‘SQL DB Contributor’ and ‘SQL Server Contributor’. Once the role that restrict Azure users from enabling 'Defender for SQL' at the resource level is in place, they may still see the 'Enable Microsoft Defender for SQL' button when navigating to 'Microsoft Defender for Cloud', but they will receive and error message if they try to enable it:
Additional information can be found at Permissions in Microsoft Defender for Cloud | Microsoft Docs
Troubleshooting:
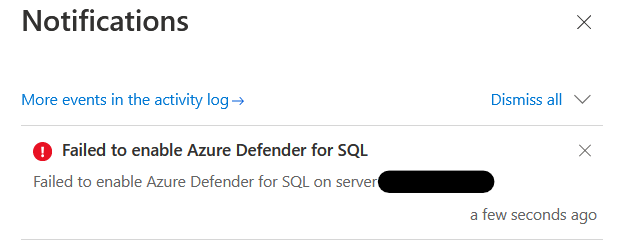
You can find below error when users try to enable SQL defender but they have no enough permissions to do so:
Here we see the http error response (400 - Bad Request) when reviewing browser development tools:
{"error":{"code":"InvalidTemplateDeployment","message":"The template deployment failed with error: 'Authorization failed for template resource 'internal-testing/Default' of type 'Microsoft.Sql/servers/securityAlertPolicies'. The client 'live.com#XXXX@outlook.com' with object id 'xxxxxxx-xxxx-xxxx-xxx-xxxxxxxx' does not have permission to perform action 'Microsoft.Sql/servers/securityAlertPolicies/write' at scope '/subscriptions/xxxxxxxxxxxxxxxxxxxx/resourceGroups/Defender-Internal/providers/Microsoft.Sql/servers/internal-testing/securityAlertPolicies/Default'.'."}}
Additional References:
Azure built-in roles - Azure RBAC | Microsoft Docs
Understand Azure role definitions - Azure RBAC | Microsoft Docs
What is Azure role-based access control (Azure RBAC)? | Microsoft Docs
Microsoft Defender for SQL - Azure SQL Database | Microsoft Docs
We hope you find this article helpful to you. If you have any feedback, please do not hesitate to provide it in the comment section below.
Ahmed S. Mazrouh / Filipe Simoes
Posted at https://sl.advdat.com/3E97FVxhttps://sl.advdat.com/3E97FVx