According to the National Institute of Standards and Technology, 21,957 vulnerabilities were published in 2021 alone. The challenge facing customers when securing their environments begins with the sheer volume and complexity of vulnerabilities and misconfigurations. Microsoft is committed to helping organizations reduce cyber risk with continuous vulnerability and misconfiguration assessment, risk-based prioritization, and built-in remediation tools.
In 2019, we announced core threat and vulnerability management tools to increase visibility and agility in managing vulnerabilities. Since then, we’ve collaborated closely with customers and design partners to better address needs spanning continuous visibility, centralized asset inventories, managing compliance with industry benchmarks, and additional mitigation activities to reduce risk during remediation.
Today, we are thrilled to announce the public preview of Microsoft Defender Vulnerability Management, a single solution offering the full set of Microsoft’s vulnerability management capabilities to help take your threat protection to the next level.
In addition to all the existing vulnerability management capabilities currently available, Defender Vulnerability Management will provide consolidated asset inventories, expanded coverage, and critical new capabilities including:
- Security baseline assessments
- Browser extension assessments
- Digital certificate assessments
- Network shares analysis
- Blocking vulnerable applications
- Vulnerability assessment for unmanaged endpoints
Microsoft Defender Vulnerability Management will be available in public preview as a standalone and as an add-on for Microsoft Defender for Endpoint Plan 2 customers.
For customers looking for a proactive, risk-based vulnerability management solution, Microsoft Defender Vulnerability Management helps you efficiently discover, assess, and remediate vulnerabilities and misconfigurations in one place. Get continuous asset visibility, consolidated inventories, intelligent assessment tools, risk-based prioritization, and built-in remediation workflows.
Sign up for the free 120-day public preview.

For Microsoft Defender for Endpoint Plan 2 customers, seamlessly enhance your vulnerability management program with the Microsoft Defender Vulnerability Management add-on. Get consolidated inventories, expanded asset coverage, cross-platform support, and new assessment and mitigation tools.
Sign up for the free 120-day public preview.
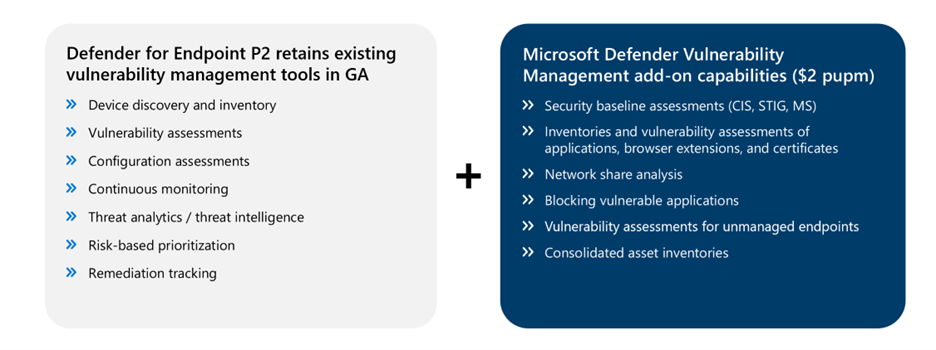
The following capabilities are now available through public preview:
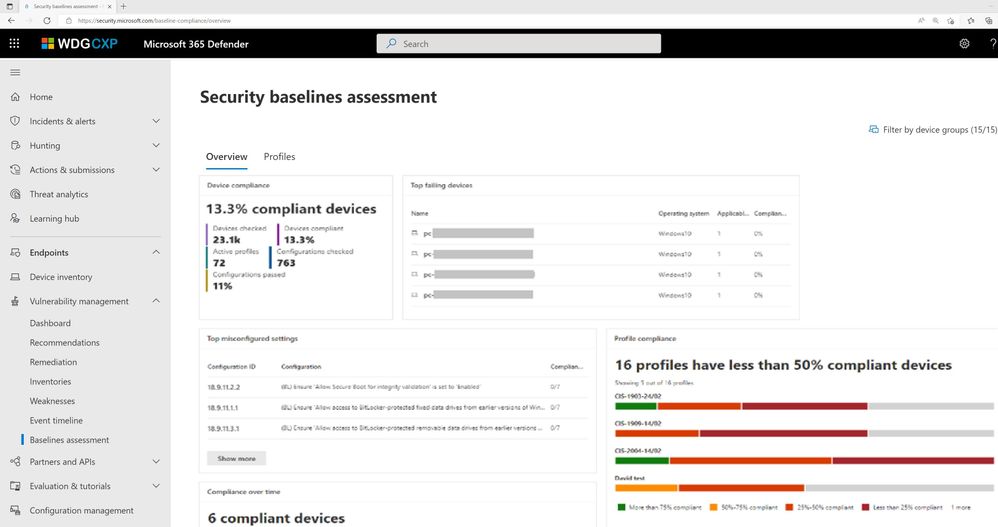
Security baselines assessments
It’s critical to proactively manage your security posture and measure risk compliance. Instead of relying on point-in-time compliance scans, continuously monitor endpoints and assess customizable baselines against industry security benchmarks in real-time. At public preview, access Center for Internet Security (CIS) benchmarks and Security Technical Implementation Guides (STIG) benchmarks. Additional support for Microsoft security benchmarks will be coming soon.
Browser extension inventory and assessments
Browser extensions are software applications that add functionality to web browsers. Extensions usually need different types of permissions to run properly – such as requiring permissions to modify a webpage. Defender Vulnerability Management’s browser extensions inventory provides detailed information on the permissions requested by each extension and identifies those with the highest associated risk levels. Customers can now leverage these risk-based assessments to make informed, contextual decisions on managing extensions in their organization’s environment.

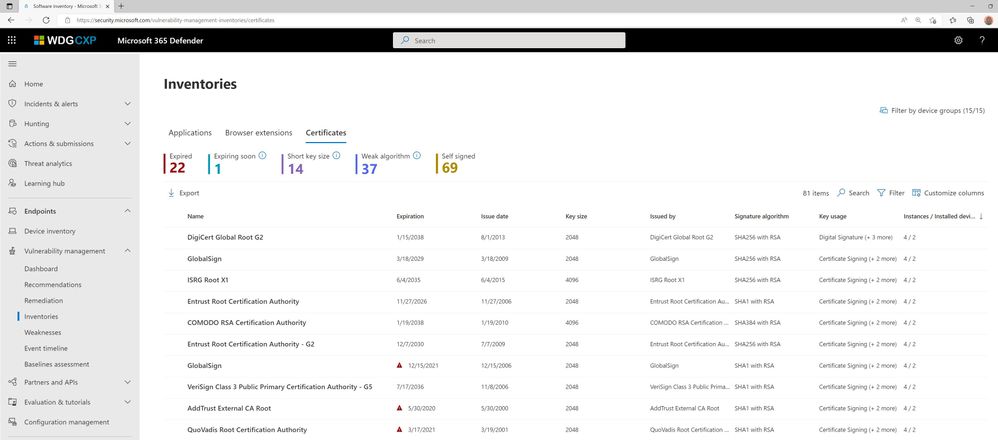
Digital certificate inventory and assessments
Digital certificates provide data encryption and authentication to ensure the secure transfer of information within your network and over the internet. Expired and misconfigured certificates can leave vulnerabilities in your organization, disrupt service, or cause outages.
The certificates inventory in Defender Vulnerability Management allows customers to easily discover, assess, and manage certificates in a single view:
- Identify certificates that are about to expire so you can update them and prevent service disruption
- Detect potential vulnerabilities due to the use of weak signature algorithms (e.g. SHA-1-RSA), short key size (e.g. RSA 512 bit) or weak signature hash algorithms (e.g. MD5)
- Ensure compliance with regulatory guidelines and organizational policies
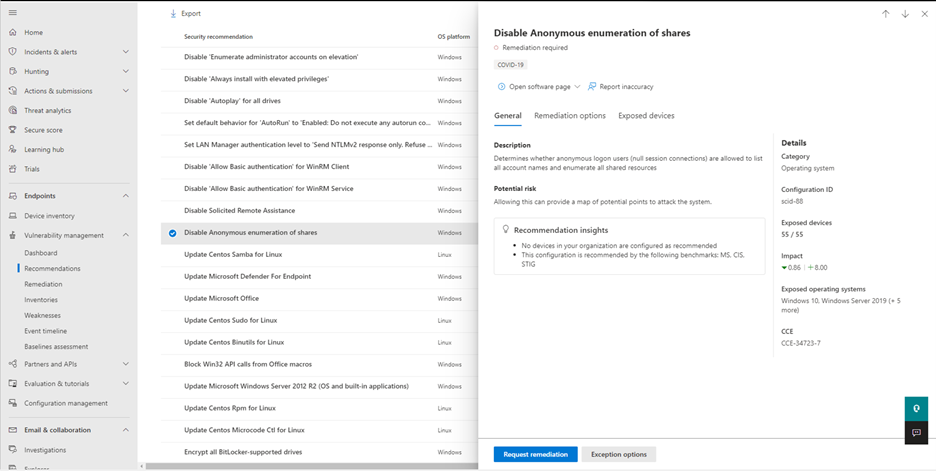
Network shares analysis
Organizations rely on internal network shares to send resources and provide access to files, documents, and media. As network shares can be easily accessed by network users, small common weaknesses can make network shares vulnerable. These types of misconfigurations are commonly used in the wild by attackers for lateral movement, reconnaissance, data exfiltration, and more. That’s why we built a new category of configuration assessments in Defender Vulnerability Management that identify the common weaknesses that expose your endpoints to attack vectors in Windows network shares.
Starting today, the following recommendations will be available as part of the new assessments:
- Disallow offline access to shares
- Remove shares from the root folder
- Remove share write permission set to ‘Everyone’
- Set folder enumeration for shares
Block vulnerable applications (Beta)
Remediating vulnerabilities in your organization can take time, but security admins can mitigate risk by taking immediate action to block all currently known vulnerable versions of applications. With Defender Vulnerability Management, customers can now block specific app versions for designated device groups, provide users with custom warning messages, and surface links to learn more on how to upgrade to approved versions.
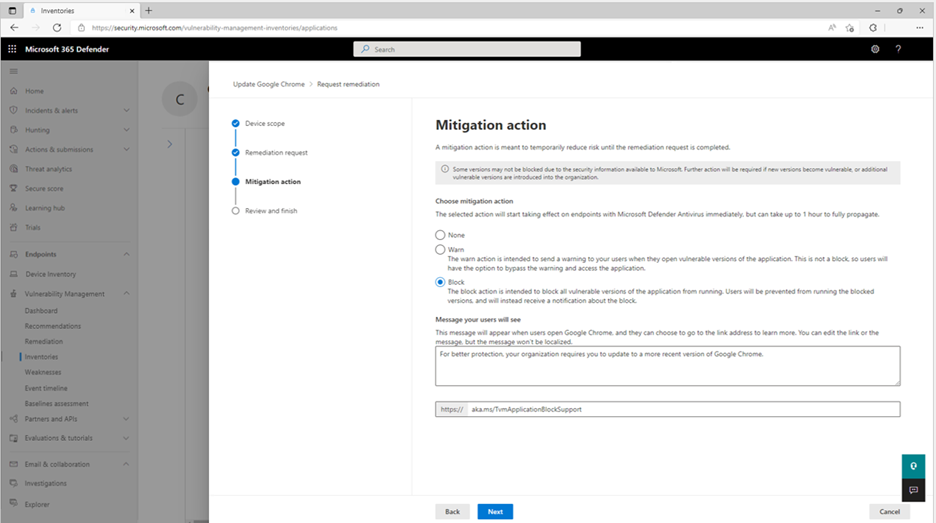
With application blocking, admins can rest easy knowing that vulnerable versions known to Microsoft are blocked on their endpoints. Additionally, admins can:
- View devices impacted by this vulnerability to allow for device scoping
- View file indicators created by this mitigation
- Export the full list of SHA 256 indicators created by a mitigation for internal reporting & validation
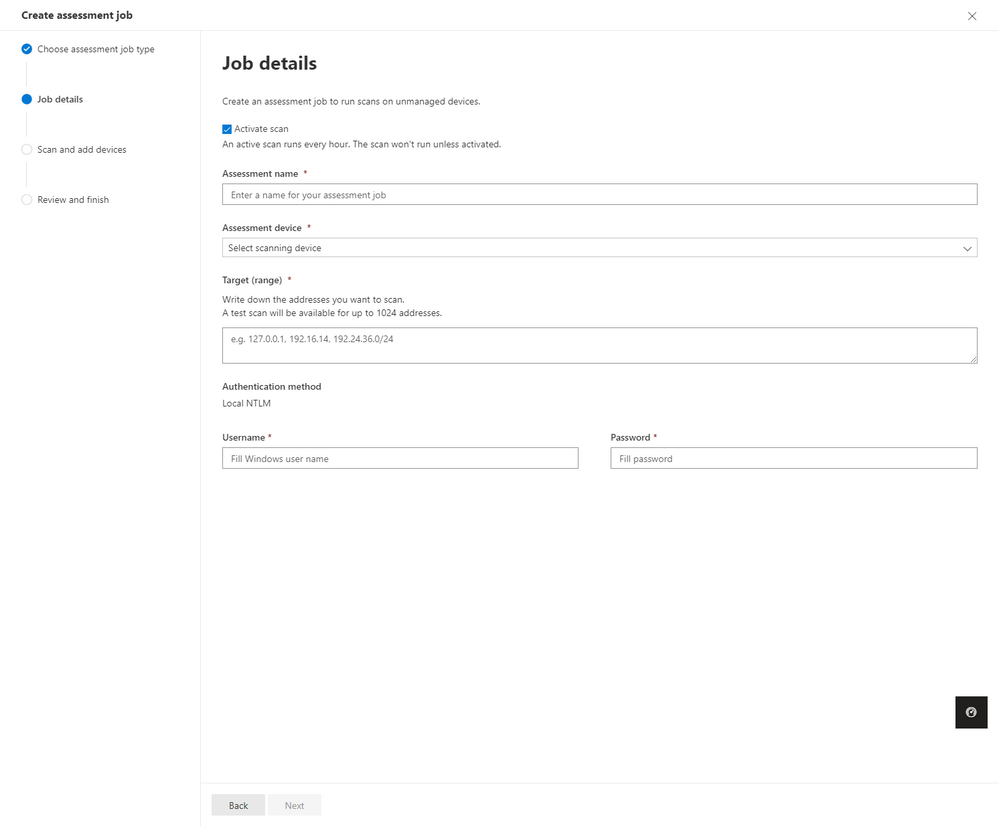
Vulnerability assessments for unmanaged endpoints (coming soon)
Comprehensive vulnerability management requires the assessment of all devices in your organization, including those that don't have Defender Vulnerability Management agents installed. When credentials are provided, Defender Vulnerability Management remotely scans unmanaged Windows devices for vulnerabilities and targets the devices by IP or range.
Capabilities include:
- Dedicated scanners to remotely access Windows devices and provide posture assessments
- Defender Vulnerability Management assessment and posture management tools for newly discovered unmanaged endpoints
- Different authenticated methods including Azure Key Vault
Note: This new capability is in private preview and will be publicly available in the next couple of weeks.
Learn more & Get started
- Sign up for public preview.
-
For customers interested in the full Defender Vulnerability Management solution, sign up here.
-
For Microsoft Defender for Endpoint Plan 2 customers interested in the Defender Vulnerability Management add-on, sign up here.
-
- Learn how to use Defender Vulnerability Management in our documentation.
- Visit our webpage and download our solution brief.
We’re excited to hear your feedback and questions! As you explore these new capabilities, please visit us on our new Tech Community page.
Posted at https://sl.advdat.com/38jZH0mhttps://sl.advdat.com/38jZH0m