Good afternoon!
Explicitly verifying identity and devices is a top priority for organizations adopting Zero Trust. For some critical operations, it’s important to be able to re-prompt the user to ensure no one is “borrowing” their device or has stolen their tokens. That’s why we’re excited to announce the public preview of re-authentication support in Azure AD Conditional Access.
Ricky Pullan, a product manager on the team, is here to tell you more and get you started!
-Alex Weinert
-----------------------------
Hey everyone! I’m Ricky Pullan, a PM on the team that worked on Conditional Access reauthentication policies, and I’m excited to help you get started. We’ve gotten a ton of feedback from customers who want extra protection during scenarios where people may have wandered away from their desks, lent their devices to their kids, or if a device became infected with token stealing malware. Our customers have given us great feedback as we co-engineered this with them, and we’re excited to get your feedback as we go into public preview.
With this new capability, you can explicitly re-verify identity, device, and any other Conditional Access conditions for high-risk scenarios. Reauthentication requires an interactive user authentication and performs all the associated policy checks for scenarios like:
- User risk
- Session risk
- Microsoft Intune device enrollment
We’ll be extending the supported scenarios over time, so stay tuned!
Getting started
Let’s say you want to require users to verify their identity by reauthenticating before they can enroll their device with Microsoft Intune. We can enable this functionality with a few quick clicks:
- Create a new Conditional Access policy
- Select the “test” group you want to include in the policy
- Select “Microsoft Intune enrollment” under “Cloud apps or actions”
- Optionally, select any other conditions for the policy
- Select the “Require multi-factor authentication” grant control
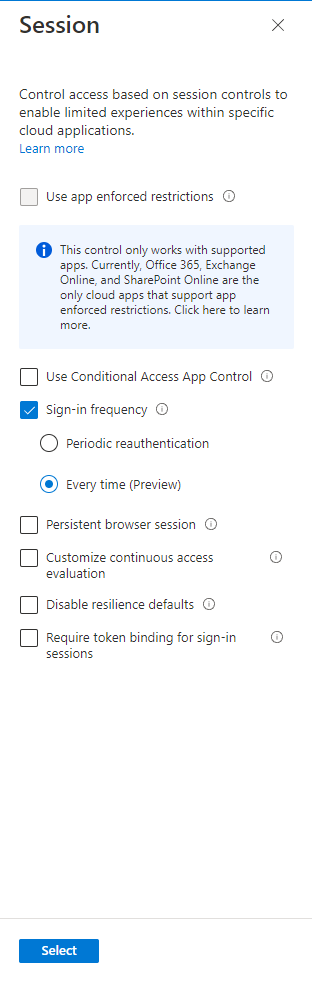
- Select “Sign-in frequency” session control and set it to “Every time”
- Enable the policy and save
Any users in the “test” group will now be required to reauthenticate when enrolling their device with Microsoft Intune if they haven’t done so within the last five minutes.
To get a better understanding of the impact these policies will have on your users, enable each policy in Report-only mode before turning on the policy for all of your users.
What’s next
We hope that this new public preview capability allows you to improve your security posture for high-risk scenarios. This release provides the best experience for passwordless end-users, but this is just the beginning! Stay tuned for announcements around expanded credential capabilities for end-users, and new reauthentication scenarios like securing VPN access, and PIM elevations. In the meantime, we'd love to hear your feedback, thoughts, and suggestions.
Learn more about Microsoft identity:
- Related Articles: Configure authentication session management with Conditional Access / Conditional Access: Session controls
- Return to the Azure Active Directory Identity blog home
- Join the conversation on Twitter and LinkedIn
- Share product suggestions on the Azure Feedback Forum