Device Inventory – The evolution of the endpoint view
Over the course of the last 12 months, we have released several new features within Microsoft Defender for Endpoint. This has enhanced the functionality of the solution and provided various key benefits to the security analysts who engage with this portal on a consistent basis. To address these changes, we have investigated ways we can improve the view within the portal, to improve the efficacy of those users when interacting with these new features.
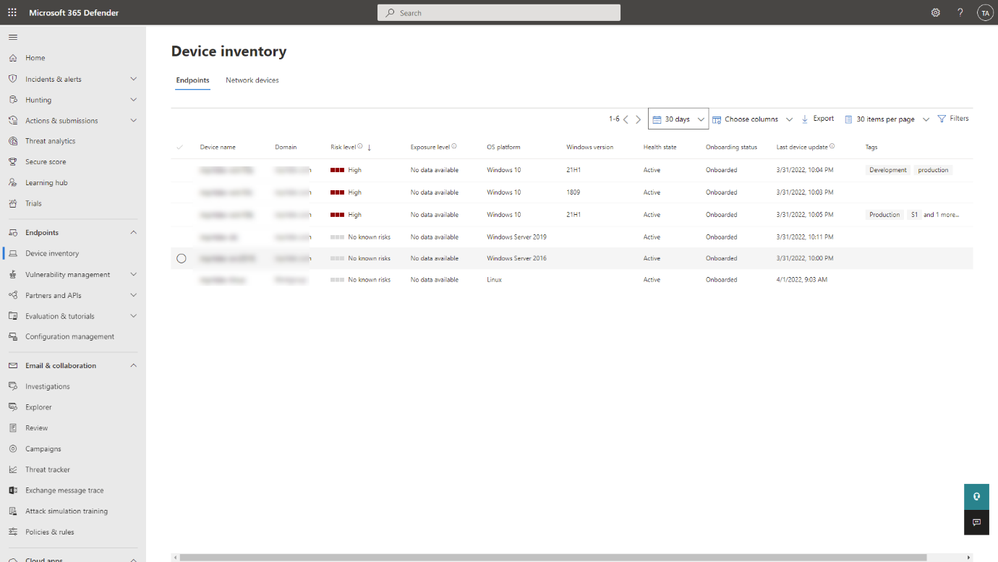
Since the introduction of Microsoft Defender for Endpoint, the Device Inventory page has remained static. The information presented only showed a list of onboarded along with some information regarding their current status, as per Figure 1.:
Figure 1: Device Inventory
We wanted to highlight not only the visual elements of the view but also the way that SOC analysts and administrators could interact with the new functionality that is now Generally Available.
New View
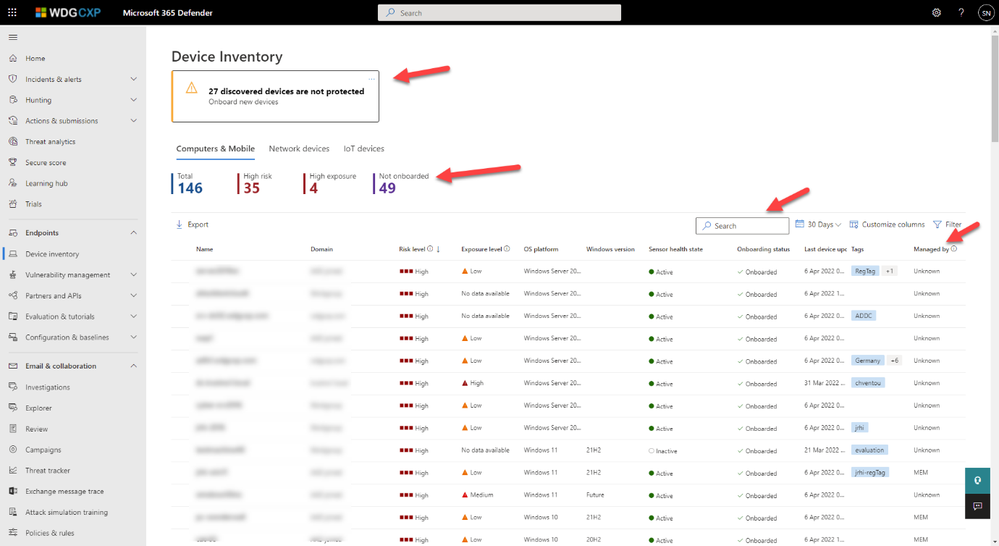
The first element we wanted to highlight is the view of the Device Inventory page itself. You can see this view in Figure 2, along with the specific elements that have been added:
Figure 2: Device Inventory Refresh
Call to Action
A key focus of the Device Inventory view was to ensure that information is presented in a way that can alert an analyst on new information to quickly trigger a response without the need to perform time-consuming investigation on the data. There are two new key elements to help with this:
- Discovered devices – Last year we introduced a feature to discover all the devices on the corporate network that were either unknown or maybe known but simply not onboarded into Microsoft Defender for Endpoint (Device discovery overview | Microsoft Docs). Previously, the way to determine if you had devices that could be onboarded would be through using the filter on the page, or through the “Onboard devices to MDE” security recommendation, but you had to actively keep checking. Analysts now have a clear view of what may be unprotected in the network, without having to go rooting around for the information.
Note: When we refer to discovered devices, this is for persistent devices in the network, it does not currently include mobile devices.
- Counts – This feature was a direct result of customer feedback. It was always possible to see how many devices there were through advanced hunting but presenting it within this view, along with counts regarding vulnerable devices, makes it much easier for an analyst to see any significant changes which may indicate a threat.
Device Exploration
In the new Device Inventory view shown in Figure 2, there are two new features to help analysts interact with the view:
- Search – The way we present search options has been one of the most requested from customers. Given this feedback, we moved the endpoint search box from the menu on the left to a more relevant and visible place. This search box will display results for endpoints either via the name of the device or its IP address. You can also use the search field at the top of the portal to search across all multiple areas of the portal, including devices, files and software.
- Managed by – This column reflects the improvements we have made around management of the endpoints. Microsoft Endpoint Manager (MEM) is the recommended solution for defining security policies on endpoints but there are different channels by which a device can be managed. A device can be fully managed by Microsoft Endpoint Manager where it will be referenced in this column as MEM, or it can be onboarded into Security Management for Microsoft Defender for Endpoint (Manage Microsoft Defender for Endpoint configuration settings on devices with Microsoft Endpoint Manager), which still uses the MEM portal but only security policies can be pushed. In which case, it will be reflected in the column as MDE. If it shows as unknown in this column, this could mean the Windows version isn’t supported for this management channel or it may be managed by SCCM or another management tool.
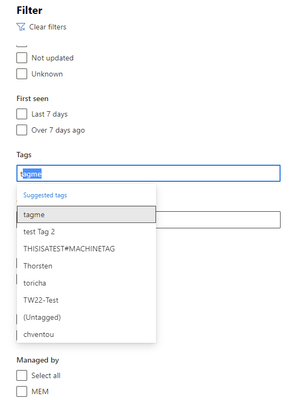
- Filters – Previously, when using filtering, specifically when filtering on tags you were presented with a long list, and it was often hard to find what you were looking for. We have modified this so that we now support auto-complete making it much easier to find what you are looking for.
We also have devices specific controls which would then be reflected in the way they are assessed and scored within other areas of the service.
- Device value – Across an organization not all devices are equal. Some of them may be low value assets, for example, a device only used for internet access and with no data. Or it may be a device directly exposed to the internet or a device owned by a VIP which you would then regard as a high value asset. There are different implications to each of these device types being compromised and so the impact to the organization would vary. The Exposure Score in the MDE portal reflects how vulnerable your organization is to cyber security threats, therefore it makes sense if your organization has a lot of high value assets, your exposure would be higher. For that reason, when we are scoring, we are assigning a weight against a device based upon the assigned value. The exact values we apply regarding the weighting can be seen in our documentation here: Assign device value - threat and vulnerability management.
Note: You can also filter this score by device groups to enable you to see which areas of your business may be more exposed than others.
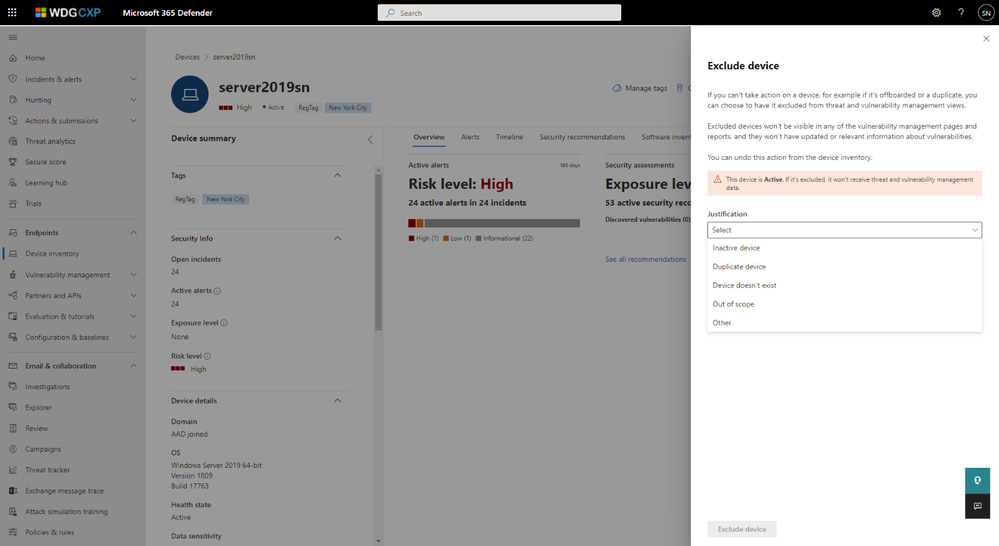
- Excluded device – If a device doesn’t report any data after 7 days it will show as inactive, and after 30 days it will stop being considered as part of the threat and vulnerability management reporting; however, there may be times when you would want a specific device excluded from reporting immediately, i.e. a device that has been decommissioned or a duplicate device. To address these scenarios, there is now an option to manually exclude a device.
By selecting this option, you can provide a justification as to why you want to exclude this device and provide any specific notes related to this exclusion. The device will then be excluded from any threat and vulnerability management reports or pages and any new information related to vulnerabilities will not be applied against this device. The device will still be present in your main Device Inventory page, meaning you have the option to stop the exclusion at any time, and have it included again within your threat and vulnerability management reports.
Getting Started
The new device inventory page is now live so there is nothing you need to do to take advantage of these new features; however, a number of these elements relate to discovered devices so we would highly recommend that you ensure you have this feature enabled. For more information, please review the documentation (Device inventory).
As you can see from the features we have introduced, we are keen to listen to all feedback and incorporate it into the development of the solution. We have plans to add even more features moving forward, including items such as making the count list on the main page clickable, also making specific functions more addressable via the API. We would love to hear your feedback both on what we have presented in this blog, but also understand if you have any further suggestions to help improve the experience.
Posted at https://sl.advdat.com/3FG7dyQhttps://sl.advdat.com/3FG7dyQ