How do you handle threat indicators in your workloads? Threat intelligence indicators are often the trigger for incident response investigations, yet many organizations struggle to ingest and make sense of their threat intelligence data. Microsoft Sentinel is a cloud native SIEM that allows customers to import threat intelligence data from various sources, including as paid threat feeds, open-source feeds (including Threat Intelligence Platforms (TIPs) across STIX & TAXII), and threat intelligence sharing communities. Threat intelligence indicators alone don’t provide significant value to security teams without operationalizing the data. As a result, once feeds are onboarded, organizations require a method to evaluate quality, health, and throughput of threat intelligence sources.
The next evolution of the Threat Intelligence Workbook to provides enhanced capabilities in both indicator ingestion and indicator search, empowering organizations to not only ingest indicators across their workloads, but also to operationalize this data for investigation and response. This solution provides a starting point for building threat intelligence programs, which require the ability to both ingest and correlate threat data across cloud workloads.
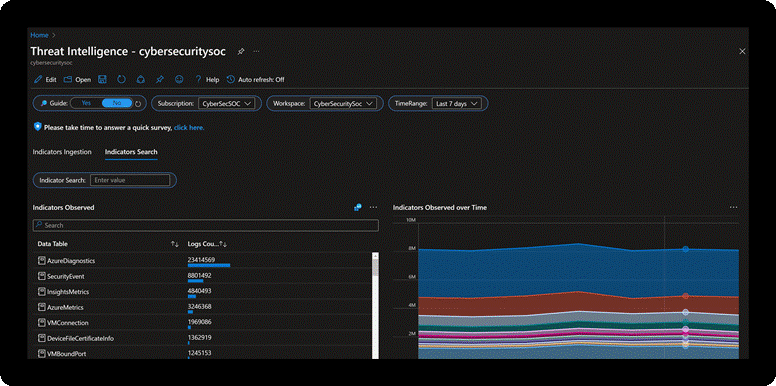
For example, indicator search provides a free-text search of indicators (IP address, file, hash, email address, username) to determine:
- Indicators in your data
- Pattern of the indicator over time
- Reporting threat intelligence feed and details
- Security Incidents for investigation and response
Use cases
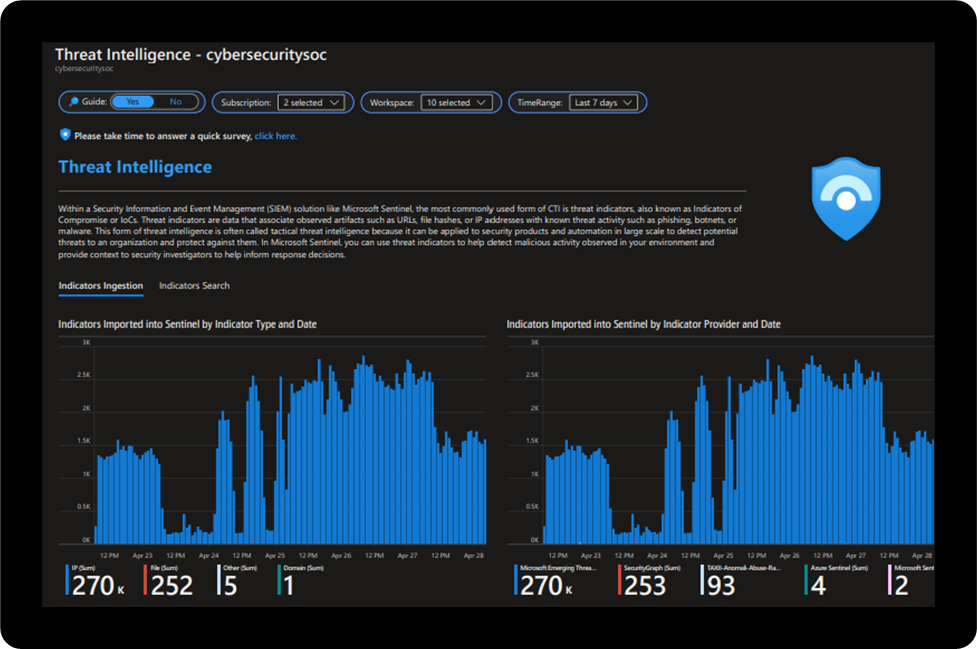
There are several use cases for the Microsoft Sentinel Threat Intelligence Workbook depending on user roles and requirements. Common use cases include threat hunting, developing alerting, and conducting research with custom reporting.
The workbook is organized into two sections:
- Indicators Ingestion: Evaluate indicators onboarded, threat feeds, and confidence ratings.
- Indicator Search: Free text search indicators across your cloud workloads.
Benefits
- Ingest, analyze, hunt for indicators within cloud, on-premises, multi-cloud, 1st/3rd party workloads
- Free text search to hunt for IPs, hash, user account, emails etc. across your data
- Investigate and respond to threat intelligence indicators
Audience
- Threat Intelligence Professionals: Investigations
- SecOps: Alert/Automation building
- MSSP: Consultants, Managed Service Providers
Getting started
- Onboard Microsoft Sentinel
- Connect Threat Intelligence Platforms
- Connect STIX/TAXII Feeds
- Update Workbook Version
- Microsoft Sentinel > Workbooks > Search “Threat Intelligence” > Select “Update” in bottom right

- Access Workbook
- Microsoft Sentinel > Threat Intelligence > Threat Intelligence Workbook

- Review the content and provide feedback through our survey
Frequently asked questions
- Why is Threat Intelligence needed?
- Correlate Cyber Threat Intelligence Indicators (CTI) observed in your workloads
- What types of indicators of compromise are included?
- Is Multi-Subscription & Multi-Tenant supported?
- Yes, via Workbook Parameters and Azure Lighthouse
- Is custom reporting available?
- Yes, via guide, time, workspace, & subscription parameters
- Is 3rd Party integration supported?
- Yes, via TAXII Connectors and Microsoft Sentinel: Incidents
- Is this available in government regions?
- Yes, Microsoft Sentinel Threat Intelligence is Generally Available in Commercial/Government regions
- Can this content be exported as a report?
- Yes, via Print Workbooks and Download Artifacts features
- Is STIX/TAXI Integrated?
- Yes, the content scales via Connectors which populate in the Threat Intelligence Indicator data table
- What if a threat indicator is observed in the workbook?
- Guide your investigation to determine where in your data the indicator was observed, determine how the indicator is classified by the threat intelligence feed, and pivot into Microsoft Sentinel Incidents for investigation/response
- What rights are required to use this content?
- Microsoft Sentinel Contributor can, create and edit workbooks, analytics rules, and other Microsoft Sentinel resources. Microsoft Sentinel Reader can view data, incidents, workbooks, and other Microsoft Sentinel resources
Learn more about Threat Intelligence with Microsoft Security
- General Availability of Microsoft Sentinel Threat Intelligence in Public and Azure Government cloud
- Understand threat intelligence in Microsoft Sentinel
- Microsoft Threat Intelligence | Unparalleled Threat Detection
Posted at https://sl.advdat.com/37ElTlthttps://sl.advdat.com/37ElTlt