As we continue to invest in Microsoft Defender for Endpoint capabilities for macOS, we are thrilled to announce the public preview of Tamper Protection for macOS devices.
Tamper Protection brings an additional layer of protection in Microsoft Defender for Endpoint to elevate the endpoint security posture of organizations. Reliably securing endpoints is crucial for any organization. Enhanced tamper resilience across prevalent platforms is a great advantage for organizations seeking to continuously enhance their endpoint security.
What are the Tamper Protection scope and prerequisites?
High level scope of Tamper Protection for macOS is:
- Prevention of unauthorized removal of Microsoft Defender for Endpoint on macOS
- Prevention of tampering with Microsoft Defender for Endpoint files, processes, and configuration
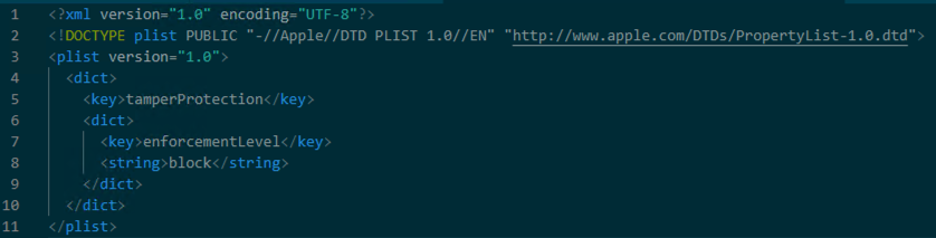
- Tamper protection for macOS can be set to “disabled”, “audit”, “block”
- Tamper protection setting applies at device level (across all users of a device).
When planning to roll out this feature, there are some key considerations and requirements to follow to ensure a successful implementation.
To experience the Tamper Protection for macOS capability in public preview, you’ll need to have preview features turned on in the Microsoft 365 Defender portal. If you have not yet opted into previews, we encourage you to turn on preview features in the Microsoft 365 Defender portal today.
IMPORTANT: While Tamper Protection capability is still in preview, ensure to only enable Tamper Protection on a designated testing group (devices, profiles, smart groups).
Know before you start:
- Supported macOS versions: Monterey (12), Big Sur (11), Catalina (10.15+)
- Minimum required version for Defender for Endpoint: 101.49.25
- Familiarity with deployment methods for Microsoft Defender for Endpoint on Mac
- Ensure that you have enabled preview features on the portal
Requirements:
- System Integrity Protection (SIP) enabled
- Mobile device management (MDM) solution to configure Microsoft Defender for Endpoint on Mac
How to enable Tamper Protection for macOS?
There are several tools and methods you can use to enable the Tamper Protection feature. The common Mac MDM solutions can be used to deploy a remote configuration that controls Tamper Protection mode. The remote configuration takes precedence over any conflicting local on-device configuration.
Microsoft Endpoint Manager and Jamf Pro are the two most used solutions when it comes to remotely configuring macOS devices.
Figure 1- How to enable tamper protection using MDM
If you are using Microsoft Endpoint Manager (formerly Intune), refer to our documented profile example to configure Tamper Protection via Microsoft Endpoint Manager: Set preferences for Microsoft Defender for Endpoint on Mac | Microsoft Docs
Figure 2- MEM configuration profile example
If you are using Jamf to configure your macOS devices, refer to our Jamf guidance Set up the Microsoft Defender for Endpoint on macOS policies in Jamf Pro | Microsoft Docs
Figure 3- Jamf configuration profile example
To enable a high degree of flexibility when configuring Tamper Protection for macOS, different modes can be applied to different groups.
There are 3 available modes in Tamper Protection:
|
Disabled |
Tamper protection is completely off (default mode at the start of the public preview) |
|
Audit |
Tampering operations are logged, but not blocked |
|
Block (recommended) |
Tamper protection is on, tampering operations are blocked |
To check which mode is enabled on a device, you can run the following command in the terminal to check the status of Tamper protection:
mdatp health ––field tamper_protection
The current Tamper Protection mode will be displayed in the tamper protection field. In the following example, the mode is set to “block”.
Figure 4- Tamper protection enabled on block mode
Where do I see Tamper Protection signals?
Tamper protection signals can be seen in Microsoft 365 Defender portal, via advanced hunting, and in local device logs.
Here are several examples of tamper protection in action:
- Defender for Endpoint agent uninstall is logged (audited)
- Editing/modification of Defender for Endpoint files are logged (audited)
- Creation of new files under Defender for Endpoint location is logged (audited)
- Deletion of Defender for Endpoint files is logged (audited)
- Renaming of Defender for Endpoint files is logged (audited)
- Commands to stop the agent failing
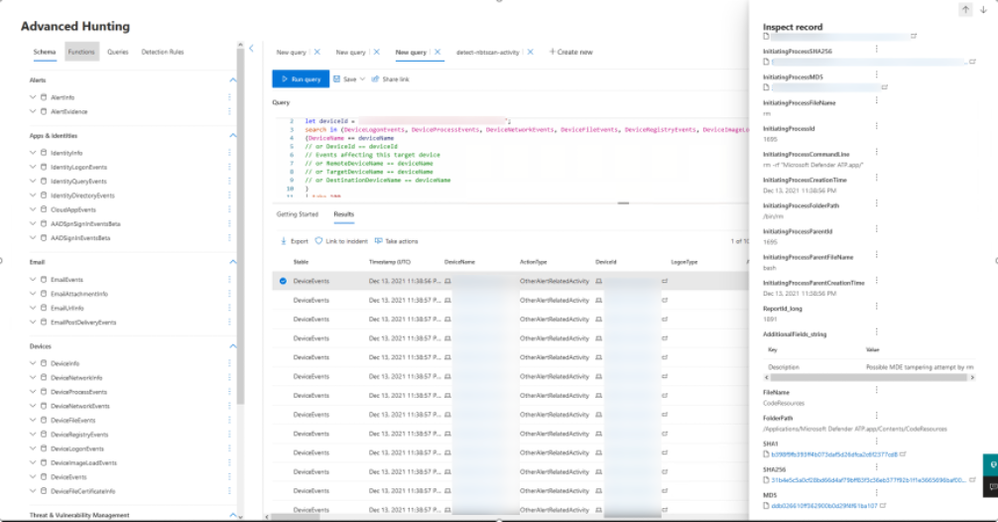
Figure 5: The following screenshot demonstrates querying for Tampering events via advanced hunting
Figure 6: This example shows an integrated Tampering alert in the M365 Defender Security Center portal
The logs can also be found locally on the device. Tampering events are logged in the following area: “Library/Logs/Microsoft/mdatp/microsoft_defender_core*.log”
Based on the logs, you can check the status of Tamper Protection using this command:
sudo grep -F '[{tamperProtection}]: Feature state:' /Library/Logs/Microsoft/mdatp/microsoft_defender_core.log | tail -n 1
Let us know what you think!
We're excited to hear your feedback on your experience with Tamper Protection on macOS. Feel free to drop a comment if you have any questions or have additional improvement suggestions!
Posted at https://sl.advdat.com/3kZg5Wzhttps://sl.advdat.com/3kZg5Wz